Advanced Configuration Strategies for Thycotic Secret Server in PAM Environments
Delving into the realm of Advanced Configuration Strategies for Thycotic Secret Server in PAM Environments opens up a world of intricate possibilities, ensuring a rich and informative journey for readers.
Providing insights and detailed explanations, this passage sets the stage for a comprehensive exploration of the topic.
Introduction to Thycotic Secret Server in PAM Environments
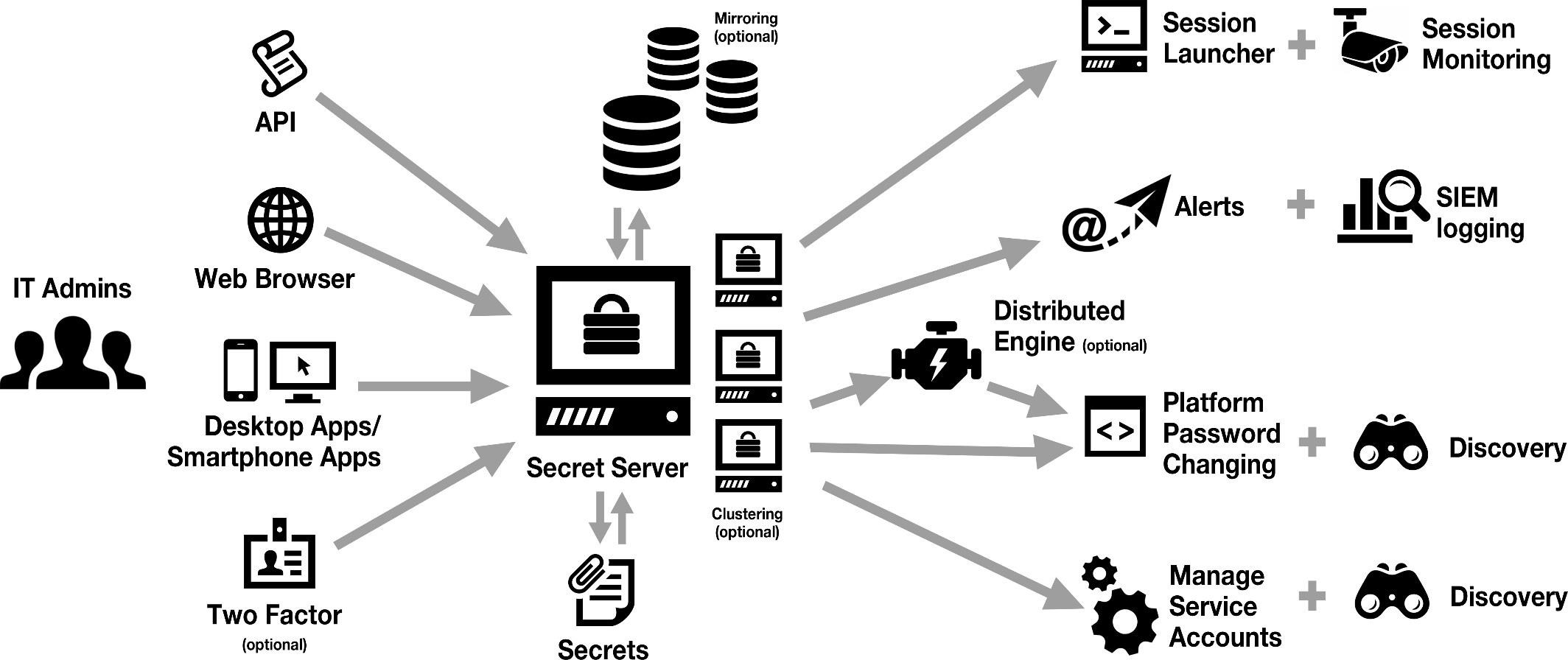
Thycotic Secret Server plays a crucial role in Privileged Access Management (PAM) environments by providing a secure platform for storing, managing, and controlling access to sensitive credentials and privileged accounts. It helps organizations mitigate the risks associated with privileged access and ensure only authorized users can access critical systems and data.
Significance of Advanced Configuration Strategies
Implementing advanced configuration strategies is essential for enhancing the security of privileged access within organizations. These strategies go beyond basic settings to strengthen access controls, improve monitoring capabilities, and streamline workflows for managing privileged accounts effectively.
- Utilizing Multi-Factor Authentication (MFA): Enhancing security by requiring multiple forms of verification before granting access to sensitive information.
- Implementing Just-In-Time Privilege Elevation: Providing temporary elevated privileges only when necessary to minimize the risk of unauthorized access.
- Integrating with SIEM Solutions: Enabling real-time monitoring and alerting to detect suspicious activities and potential security incidents.
- Leveraging Automated Password Rotation: Enhancing security by automatically changing passwords at regular intervals to reduce the risk of credential misuse.
Key Features of Thycotic Secret Server
Thycotic Secret Server offers a range of key features that make it a standout solution in the Privileged Access Management (PAM) space. Let's dive into some of the essential features that set Thycotic Secret Server apart from other PAM solutions in the market.
Centralized Credential Management
Thycotic Secret Server provides a centralized platform for managing and storing sensitive credentials, such as passwords, SSH keys, and API keys. This centralized approach improves security by ensuring that all credentials are stored in a secure location, reducing the risk of unauthorized access.
Role-based Access Control
With Thycotic Secret Server, administrators can implement role-based access control to restrict access to sensitive information based on users' roles and responsibilities. This granular control helps organizations enforce the principle of least privilege, minimizing the risk of insider threats.
Automated Password Rotation
Thycotic Secret Server offers automated password rotation capabilities, allowing organizations to regularly rotate passwords for critical systems and accounts. This feature helps enhance security by reducing the likelihood of unauthorized access due to compromised credentials.
Integration Capabilities
Thycotic Secret Server integrates seamlessly with a wide range of third-party tools and systems, including SIEM solutions, ticketing systems, and multi-factor authentication providers. This flexibility enables organizations to incorporate Thycotic Secret Server into their existing IT environments without disruption.
Audit and Compliance Reporting
Thycotic Secret Server provides robust audit and compliance reporting features, allowing organizations to track user activities, access to sensitive information, and changes made to credentials. These reports help organizations demonstrate compliance with regulatory requirements and internal security policies.
Advanced Configuration Strategies

When it comes to advanced configuration settings in Thycotic Secret Server, there are several key options that can help optimize the platform for complex Privileged Access Management (PAM) environments. These settings go beyond the basic configurations and provide additional layers of security and control.
Custom Password Policies
- Thycotic Secret Server allows administrators to create custom password policies based on specific requirements of the organization. This includes setting password length, complexity, expiration, and reuse rules.
- By implementing custom password policies, organizations can ensure that all privileged accounts adhere to strict security standards, reducing the risk of unauthorized access.
Role-based Access Control
- One advanced configuration feature in Thycotic Secret Server is role-based access control (RBAC), which allows for granular control over who can access and manage sensitive information within the platform.
- By defining roles with specific permissions, organizations can restrict access to sensitive data to only authorized users, reducing the chances of data breaches or misuse.
Integration with SIEM Solutions
- Thycotic Secret Server offers integration with Security Information and Event Management (SIEM) solutions, enabling organizations to centralize and analyze security event data from multiple sources.
- By integrating Thycotic Secret Server with SIEM solutions, organizations can gain better visibility into privileged account activities, detect suspicious behavior, and respond to security incidents more effectively.
Integration with PAM Environments
Thycotic Secret Server offers seamless integration with existing PAM tools and frameworks, allowing organizations to enhance their privileged access management capabilities.
Setting up Integration with Thycotic Secret Server
To set up seamless integration between Thycotic Secret Server and other PAM solutions, follow these steps:
- First, identify the PAM solution you want to integrate with Thycotic Secret Server.
- Access the Thycotic Secret Server administration console and navigate to the integration settings.
- Select the option to integrate with a PAM solution and follow the on-screen instructions to configure the integration.
- Ensure that the necessary permissions and credentials are provided to establish a secure connection between Thycotic Secret Server and the PAM solution.
- Test the integration to ensure that privileged access management tasks can be seamlessly performed across both platforms.
Role-Based Access Control (RBAC) Implementation

Role-Based Access Control (RBAC) plays a crucial role in securing privileged access within an organization. By assigning permissions based on roles rather than individual users, RBAC ensures that users only have access to the resources necessary for their specific job functions, reducing the risk of unauthorized access and potential security breaches.
Designing a Comprehensive RBAC Strategy with Thycotic Secret Server
Implementing RBAC with Thycotic Secret Server involves creating roles, defining permissions, and assigning users to these roles. Here is a comprehensive strategy for designing an effective RBAC system using Thycotic Secret Server:
- Identify Organizational Roles: Begin by identifying the different roles within your organization, such as administrators, IT staff, and business users. Each role should have specific responsibilities and access requirements.
- Create Role-Based Policies: Define policies that Artikel the permissions and access levels associated with each role. These policies should be based on the principle of least privilege, granting users only the access they need to perform their job functions.
- Implement Role-Based Access Controls: Utilize Thycotic Secret Server's RBAC features to assign roles to users and manage their access permissions. Regularly review and update these assignments to ensure they align with organizational changes.
- Enforce Separation of Duties: Implement separation of duties by ensuring that critical tasks require multiple roles to complete. This reduces the risk of fraud or errors by preventing a single user from having full control over sensitive operations.
- Monitor and Audit Access: Regularly monitor user access and conduct audits to ensure compliance with RBAC policies. Thycotic Secret Server offers reporting capabilities that allow you to track user activity and identify any unauthorized access attempts.
By implementing a well-designed RBAC strategy with Thycotic Secret Server, organizations can effectively manage and control privileged access, reducing the risk of security incidents and ensuring compliance with regulatory requirements.
Auditing and Monitoring Capabilities
Thycotic Secret Server offers robust auditing and monitoring features to track privileged access activities effectively.
Audit Logs
- Thycotic Secret Server generates detailed audit logs for all user activities, providing visibility into who accessed which secrets and when.
- The audit logs capture changes made to secrets, access requests, approvals, and denials, helping organizations maintain compliance and enhance security.
- These logs can be customized to include specific events or actions based on organizational requirements.
Monitoring Tools
- Thycotic Secret Server integrates with monitoring tools like SIEM platforms to provide real-time alerts and notifications for suspicious activities.
- Administrators can set up triggers and thresholds to alert on specific events, enabling proactive response to potential security threats.
- Monitoring tools help organizations detect unauthorized access, unusual patterns, and potential security breaches in a timely manner.
Final Thoughts
In conclusion, the discussion on Advanced Configuration Strategies for Thycotic Secret Server in PAM Environments unveils the importance of robust security measures and strategic configurations in privileged access management.