Optimizing Thycotic Secret Server for Compliance and Cybersecurity: A Comprehensive Guide
Exploring the realm of Optimizing Thycotic Secret Server for Compliance and Cybersecurity, this introduction sets the stage for an in-depth discussion that captures the essence of securing privileged account passwords and meeting compliance standards.
Detailing the steps involved in configuring Thycotic Secret Server and the benefits it offers in enhancing cybersecurity, this guide aims to provide valuable insights for organizations looking to bolster their security measures.
Overview of Thycotic Secret Server
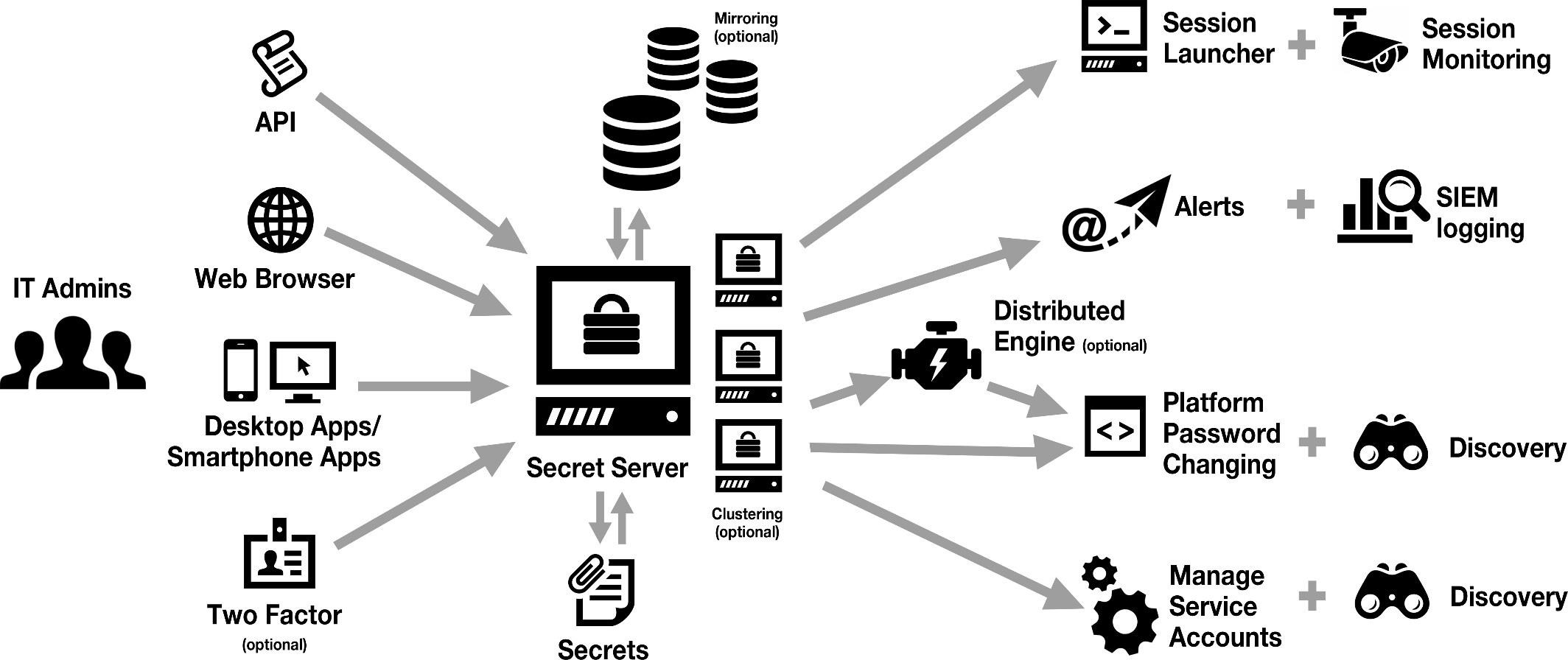
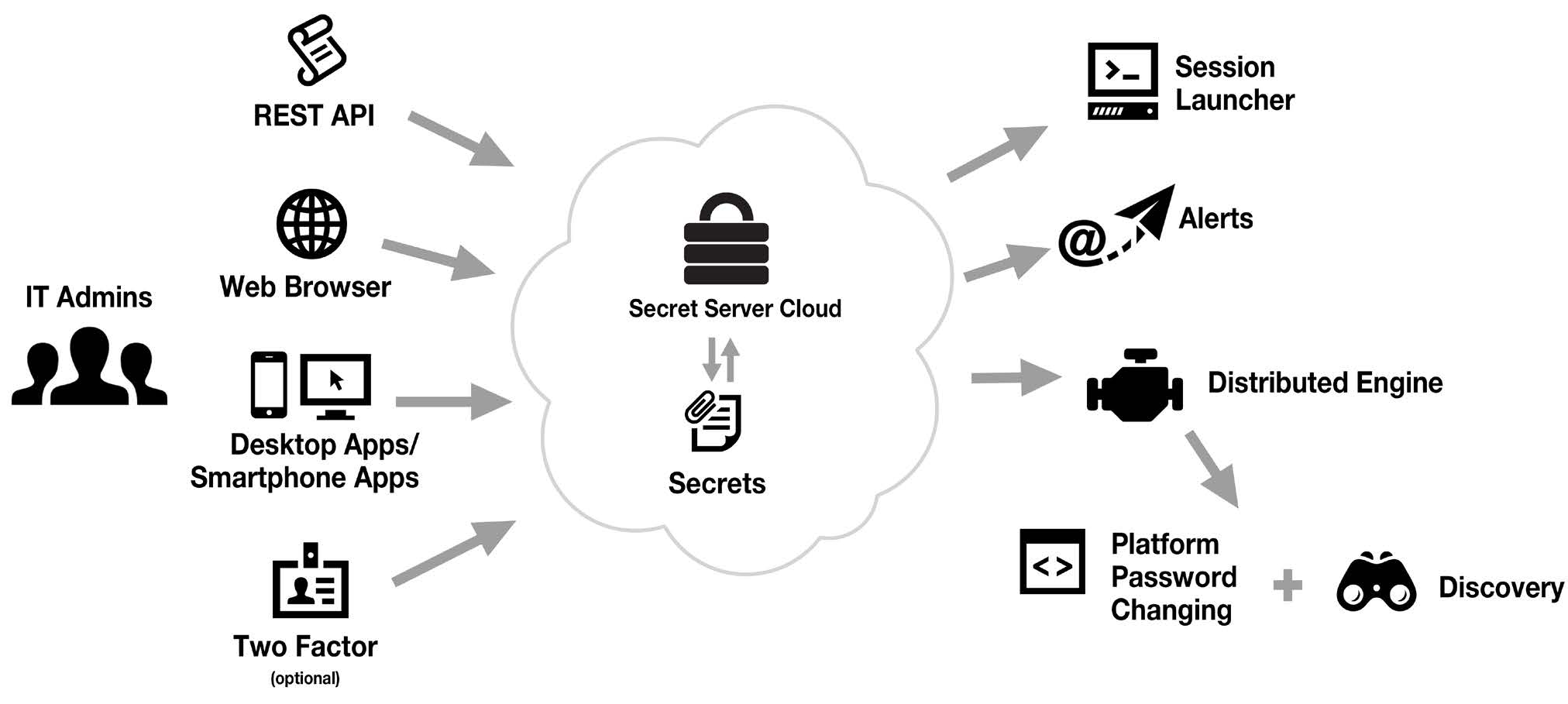
Thycotic Secret Server is a privileged access management solution designed to secure and manage sensitive information, such as passwords, across an organization. It helps in protecting critical data by centralizing and controlling access to privileged accounts.
Functionality of Thycotic Secret Server
Thycotic Secret Server offers features like password management, session monitoring, and access control to ensure that only authorized users can access sensitive data. It also provides auditing and reporting capabilities to track user activity and ensure compliance with security standards.
Examples of Industries Using Thycotic Secret Server
- Financial Services: Banks, insurance companies, and investment firms utilize Thycotic Secret Server to safeguard customer data and comply with regulations like PCI DSS.
- Healthcare: Hospitals, clinics, and healthcare providers use Thycotic Secret Server to protect patient information and adhere to HIPAA regulations.
- Government Agencies: Federal, state, and local government organizations rely on Thycotic Secret Server to secure sensitive data and meet compliance requirements.
- Technology Companies: Tech firms and software developers use Thycotic Secret Server to protect intellectual property and ensure secure access to critical systems.
Importance of Compliance in Cybersecurity
Compliance regulations play a vital role in ensuring the security and integrity of an organization's data and systems. These regulations are designed to establish guidelines and standards that organizations must adhere to in order to protect sensitive information and prevent cyber threats.
Significance of Compliance Regulations
Compliance standards have a direct impact on organizations' cybersecurity practices by providing a framework for implementing security controls, monitoring systems, and mitigating risks. Non-compliance can result in severe consequences, including financial penalties, legal actions, and reputational damage.
- Compliance frameworks such as GDPR (General Data Protection Regulation), HIPAA (Health Insurance Portability and Accountability Act), and PCI DSS (Payment Card Industry Data Security Standard) are some common examples of regulations that organizations need to comply with to ensure data protection and cybersecurity.
- These frameworks Artikel specific requirements and best practices that organizations must follow to safeguard sensitive data, secure their networks, and prevent unauthorized access.
- By aligning with compliance standards, organizations can enhance their cybersecurity posture, build trust with customers, and demonstrate a commitment to protecting data privacy and security.
Optimizing Thycotic Secret Server for Compliance
When it comes to optimizing Thycotic Secret Server for compliance, there are several key steps that need to be taken in order to ensure that your organization meets the necessary requirements. Thycotic Secret Server provides a robust platform that can help streamline compliance efforts and enhance cybersecurity.
Configuring Thycotic Secret Server for Compliance
Configuring Thycotic Secret Server to meet compliance requirements involves several steps, including:
- Setting up role-based access controls to limit access to sensitive information.
- Enforcing strong password policies to ensure secure credentials management.
- Implementing audit trails to track all activities and changes within the system.
- Integrating with existing IT infrastructure to centralize and secure all privileged account credentials.
Achieving Compliance with Thycotic Secret Server
Thycotic Secret Server aids in achieving compliance with various standards such as PCI DSS, HIPAA, GDPR, and more by:
- Providing encryption capabilities to protect sensitive data.
- Offering detailed reporting and monitoring features for compliance audits.
- Automating password rotations and expirations to ensure regulatory requirements are met.
- Facilitating regular security assessments and vulnerability scans to maintain compliance.
Best Practices for Optimizing Thycotic Secret Server
When optimizing Thycotic Secret Server for compliance, it is important to follow these best practices:
- Regularly update and patch the software to address any security vulnerabilities.
- Train employees on proper password management and security protocols.
- Implement multi-factor authentication to add an extra layer of security to sensitive data.
- Conduct regular compliance assessments to ensure ongoing adherence to standards.
Enhancing Cybersecurity with Thycotic Secret Server

Thycotic Secret Server plays a crucial role in enhancing cybersecurity posture by providing robust security features and controls to protect sensitive data and credentials from unauthorized access and cyber threats.
Cybersecurity Benefits of Using Thycotic Secret Server
- Centralized Access Control: Thycotic Secret Server allows organizations to centralize and manage access to privileged accounts, reducing the risk of unauthorized access.
- Encryption: The platform encrypts sensitive data such as passwords, ensuring that even if the data is compromised, it remains secure and unreadable.
- Audit Trails: Thycotic Secret Server provides detailed audit trails, allowing organizations to track and monitor access to privileged accounts for compliance and security purposes.
- Automated Password Rotation: The platform automates the process of password rotation, reducing the risk of password-related security incidents.
Security Features in Thycotic Secret Server
- Role-Based Access Control:Thycotic Secret Server enables organizations to assign roles and permissions to users based on their responsibilities, limiting access to sensitive information.
- Two-Factor Authentication:The platform supports two-factor authentication, adding an extra layer of security to verify users' identities before granting access.
- Session Recording:Thycotic Secret Server records and monitors user sessions, allowing organizations to review user activities and detect any suspicious behavior.
- Vaulting:The platform securely stores and manages privileged account credentials in a centralized vault, protecting them from unauthorized access.
Integration with Other Security Tools
Integrating Thycotic Secret Server with other cybersecurity tools is crucial in enhancing overall security posture and ensuring comprehensive protection of sensitive data. By seamlessly connecting Thycotic Secret Server with a variety of security solutions, organizations can strengthen their defense mechanisms and improve incident response capabilities.
Benefits of Integration with SIEM Platforms
Integrating Thycotic Secret Server with Security Information and Event Management (SIEM) platforms offers several advantages in terms of monitoring, detecting, and responding to security incidents effectively.
- Enhanced Visibility: Integration enables real-time monitoring of privileged account usage and access, providing insights into potential security threats.
- Automated Alerting: SIEM integration allows for automated alerts and notifications based on predefined security policies, facilitating prompt incident response.
- Centralized Reporting: By combining Thycotic Secret Server data with SIEM logs, organizations can generate comprehensive reports for compliance audits and forensic investigations.
Streamlining Cybersecurity Operations
Integrating Thycotic Secret Server with other security tools streamlines cybersecurity operations and optimizes overall efficiency in managing privileged access.
- Single Pane of Glass: Integration with tools like Identity Access Management (IAM) platforms provides a centralized view of user access rights and permissions, simplifying access control.
- Automated Workflows: Integration with ticketing systems automates password reset requests and access approvals, reducing manual intervention and improving operational agility.
- Threat Intelligence Integration: Combining Thycotic Secret Server with threat intelligence feeds enhances threat detection capabilities and enables proactive defense against emerging cyber threats.
Final Conclusion
In conclusion, Optimizing Thycotic Secret Server for Compliance and Cybersecurity is a crucial aspect of modern cybersecurity practices. By implementing best practices and integrating with other security tools, organizations can fortify their defenses and safeguard sensitive data effectively.