Comprehensive Guide to Thycotic Secret Server Implementation for Enterprises
Embark on a journey through the Comprehensive Guide to Thycotic Secret Server Implementation for Enterprises, delving into the intricacies of implementing this powerful tool within enterprise settings. This comprehensive guide offers valuable insights and practical advice to streamline the process effectively.
Explore the key steps, considerations, and best practices for a successful Thycotic Secret Server implementation tailored to the unique needs of enterprises.
Overview of Thycotic Secret Server Implementation

Thycotic Secret Server is a privileged access management solution designed to safeguard sensitive data and credentials within an organization. It offers a secure and centralized platform for managing, sharing, and protecting privileged account passwords and other critical information.Implementing Thycotic Secret Server is crucial for enterprises to enhance security measures and prevent unauthorized access to sensitive data.
By utilizing this solution, organizations can enforce strict access controls, track user activity, and ensure compliance with regulatory requirements.
Key Features of Thycotic Secret Server for Enterprise Use
- Centralized Password Management: Thycotic Secret Server provides a centralized repository for storing and managing passwords, reducing the risk of password sprawl and unauthorized access.
- Role-based Access Control: Enterprises can define granular access levels based on roles and responsibilities, ensuring that users only have access to the information they need.
- Audit Trails and Reporting: Thycotic Secret Server offers detailed audit trails and reporting capabilities, allowing organizations to track user activity and monitor access to sensitive data.
- Automated Password Rotation: The solution enables automated password rotation for privileged accounts, reducing the likelihood of password-related security incidents.
- Integration Capabilities: Thycotic Secret Server integrates with a wide range of third-party applications and systems, providing a seamless user experience and enhancing overall security posture.
Planning for Thycotic Secret Server Implementation
Planning for the implementation of Thycotic Secret Server is a crucial step to ensure a successful deployment within an enterprise environment. This involves various steps and considerations to tailor the solution according to the organization's specific needs.
Steps Involved in Planning
- Assess current security policies and practices to identify areas where Thycotic Secret Server can enhance data protection.
- Define the scope of the implementation, including the number of users, types of secrets to be stored, and integration with existing systems.
- Conduct a thorough evaluation of the infrastructure to ensure compatibility with Thycotic Secret Server requirements.
- Create a detailed project plan outlining timelines, resource allocation, and key milestones for the implementation.
Key Stakeholders Involved
- IT Security Team: Responsible for overseeing the implementation and ensuring compliance with security standards.
- System Administrators: Involved in configuring the solution, setting up user access, and managing day-to-day operations.
- Department Heads: Provide insights into department-specific requirements and use cases for Thycotic Secret Server.
- Executive Sponsor: Provides leadership and support to ensure the successful implementation of the solution.
Considerations for Customization
- Customizing access controls and permissions based on the organization's hierarchy and data sensitivity.
- Integrating with existing identity management systems for seamless user authentication and authorization.
- Configuring automated workflows for secret rotation, access approval, and auditing based on enterprise policies.
- Implementing multi-factor authentication to enhance security for accessing sensitive information stored in Thycotic Secret Server.
Installation and Configuration
When it comes to installing and configuring Thycotic Secret Server, it is essential to follow a systematic approach to ensure a smooth setup process and optimal performance. Below, we will detail the installation process, explain the configuration options available during setup, and provide best practices for configuring Thycotic Secret Server.
Installation Process
Installing Thycotic Secret Server involves the following steps:
- Download the installation package from the Thycotic website.
- Run the installer and follow the on-screen instructions.
- Choose the installation directory and configure the database settings.
- Complete the installation process and set up the initial administrator account.
Configuration Options
During the setup of Thycotic Secret Server, you will encounter various configuration options, including:
- Setting up user roles and permissions for access control.
- Configuring email notifications for alerts and reporting.
- Integrating with LDAP or Active Directory for user authentication.
- Customizing password complexity rules and expiration policies.
Best Practices for Configuration
To ensure optimal performance of Thycotic Secret Server, consider the following best practices for configuration:
- Regularly update the software to the latest version to benefit from new features and security enhancements.
- Implement strong encryption protocols to protect sensitive data stored in the server.
- Monitor server performance and usage to identify any potential bottlenecks or issues.
- Backup the server regularly to prevent data loss in case of system failures.
Integration with Existing Systems

Integrating Thycotic Secret Server with other systems is crucial for ensuring a seamless workflow and maximizing security measures within an enterprise. By integrating Thycotic Secret Server with existing systems, organizations can centralize access control, enhance security protocols, and streamline user management processes.
Common Systems for Integration
- Active Directory
- LDAP
- Azure AD
- SIEM solutions
- Ticketing systems
Integration with Active Directory
Integrating Thycotic Secret Server with Active Directory is essential for managing user access and permissions effectively. Here is a step-by-step guide to integrate Thycotic Secret Server with Active Directory:
- Log in to Thycotic Secret Server as an administrator.
- Navigate to Administration > Configuration > User Directories.
- Click on "Add New" and select Active Directory as the directory type.
- Enter the required Active Directory details such as domain, user account, and password.
- Test the connection to ensure successful integration.
- Map Active Directory groups to Secret Server roles for access control.
- Synchronize user accounts from Active Directory to Thycotic Secret Server.
- Monitor and manage user access rights through the integrated Active Directory.
User Management and Access Control
User management and access control are crucial components of Thycotic Secret Server that help organizations secure their sensitive information effectively.
User Management Capabilities
Thycotic Secret Server offers robust user management capabilities, allowing administrators to create, modify, and deactivate user accounts easily
- Administrators can create custom user roles with specific permissions tailored to the organization's needs.
- Users can be grouped based on their roles and responsibilities, simplifying access control management.
- Multi-factor authentication options enhance user authentication and security.
Access Control Mechanisms
Thycotic Secret Server provides various access control mechanisms to secure sensitive information and prevent unauthorized access.
- Role-based access control (RBAC) ensures that users only have access to the information necessary for their roles.
- Granular access control settings allow administrators to define access levels at the individual user or group level.
- Audit logs track user activity, providing visibility into who accessed what information and when.
Setting Up User Roles and Permissions
Effective setup of user roles and permissions is essential for maintaining security and controlling access to sensitive information within Thycotic Secret Server.
- Start by defining clear user roles based on job responsibilities and access needs.
- Assign permissions carefully, following the principle of least privilege to restrict access to only necessary information.
- Regularly review and update user roles and permissions to align with organizational changes and ensure ongoing security.
Monitoring and Auditing
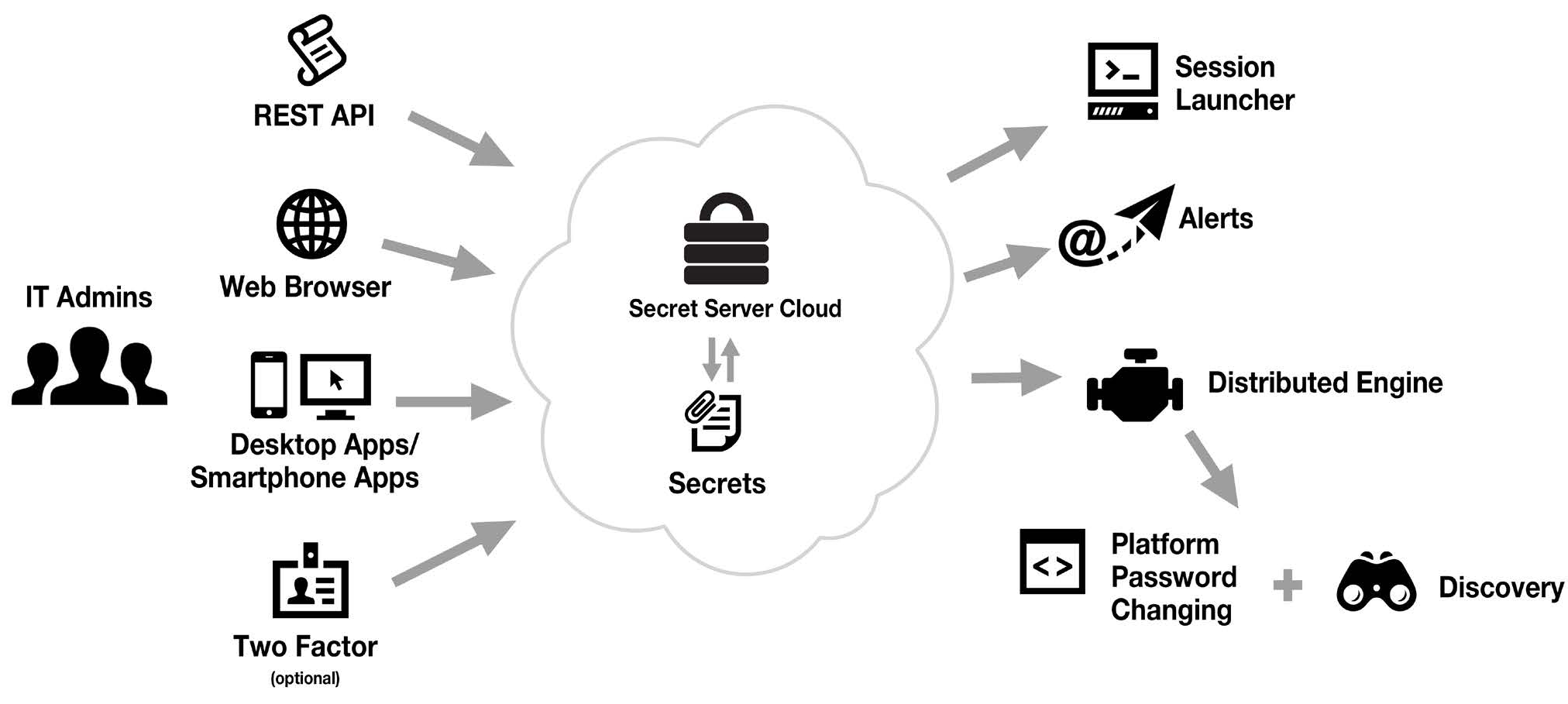
Monitoring and auditing are critical components of maintaining the security of sensitive information within Thycotic Secret Server. These features allow organizations to track access to secrets, monitor changes made, and generate reports for compliance and security audits.
Monitoring Features
Thycotic Secret Server offers robust monitoring features that provide real-time insights into user activities within the system. Key monitoring functionalities include:
- Tracking of user login/logout activities
- Monitoring of secret access and usage
- Alerts for unauthorized access attempts
Auditing Capabilities
Thycotic Secret Server's auditing capabilities enable organizations to track access to secrets and changes made by users. This helps in maintaining accountability and identifying any suspicious activities. Key auditing features include:
- Logging of all user actions within the system
- Recording of changes to secrets, including who made the changes and when
- Integration with SIEM tools for centralized log management
Generating Reports
Thycotic Secret Server allows organizations to generate comprehensive reports for compliance and security audits. These reports provide detailed insights into user activities, access controls, and changes made to secrets. Organizations can customize reports based on their specific requirements and export them in various formats for sharing and analysis.
Backup and Disaster Recovery
When it comes to Thycotic Secret Server implementation, having a solid backup and disaster recovery plan is crucial to ensure the security and availability of sensitive data. In this section, we will explore the backup strategies for Thycotic Secret Server data and discuss the disaster recovery options in case of system failures.
Backup Strategies
- Regular backups: Schedule automated backups of Thycotic Secret Server data on a daily or weekly basis to ensure that the most up-to-date information is always available.
- Offsite backups: Store backup copies of the data in an offsite location to protect against physical damage or theft of the primary server.
- Encryption: Encrypt the backup files to ensure that sensitive information remains secure even in the event of a breach.
Disaster Recovery Options
- Failover systems: Implement failover systems to quickly switch to backup servers in case of a primary system failure, ensuring minimal downtime.
- Data replication: Set up data replication to mirror critical information in real-time to another server, providing redundancy in case of data loss.
- Disaster recovery plan: Create a detailed disaster recovery plan outlining steps to be taken in the event of a system failure, including roles and responsibilities of team members.
Restoring Data from Backups
- Identify the latest backup: Determine the most recent backup that contains the data needed for restoration.
- Access backup files: Retrieve the backup files from the designated storage location.
- Restore data: Follow the step-by-step instructions provided by Thycotic Secret Server to restore the data from the backup files to the primary server.
- Verify data integrity: Verify that the restored data is accurate and complete to ensure that all information is successfully recovered.
Training and Support
Training and support are crucial components of a successful Thycotic Secret Server implementation for enterprises. Let's explore the available resources and options provided by Thycotic to ensure a smooth deployment and ongoing maintenance.
Training Resources
Thycotic offers comprehensive training resources for Secret Server users, including online tutorials, documentation, webinars, and in-person training sessions. These resources cover a wide range of topics, from basic user training to advanced configuration and customization.
- Online Tutorials: Step-by-step guides and video tutorials for users to learn at their own pace.
- Documentation: Detailed manuals and guides for reference and troubleshooting.
- Webinars: Live and recorded webinars on specific features and best practices for Secret Server.
- In-person Training: Hands-on training sessions conducted by Thycotic experts for a more interactive learning experience.
It is recommended that users take advantage of these training resources to maximize their understanding and utilization of Thycotic Secret Server.
Support Options
Thycotic provides various support options for enterprise customers to ensure timely assistance and resolution of issues. Support options may include email support, phone support, online chat, and a dedicated support portal.
- Email Support: Submitting support tickets via email for non-urgent issues.
- Phone Support: Direct access to support representatives for immediate assistance with critical issues.
- Online Chat: Real-time chat support for quick questions and troubleshooting.
- Support Portal: Access to resources, FAQs, and updates for self-service support.
For enterprise customers, it is advisable to choose a support plan that aligns with their needs and ensures prompt resolution of any technical challenges.
Recommendations for Ongoing Training and Support
To ensure a successful implementation and continued efficiency of Thycotic Secret Server, it is recommended that enterprises prioritize ongoing training and support. Regularly scheduled training sessions, participation in webinars, and maintaining a support contract with Thycotic can help address any evolving needs and optimize the use of Secret Server within the organization.
- Schedule Regular Training Sessions: Conduct periodic training sessions for new users and refresher courses for existing users.
- Participate in Webinars: Stay updated on new features and best practices by actively participating in Thycotic's webinars.
- Maintain Support Contract: Ensure continuous access to support resources by renewing or upgrading support contracts as needed.
Final Conclusion
In conclusion, the Comprehensive Guide to Thycotic Secret Server Implementation for Enterprises equips businesses with the knowledge and tools necessary to optimize their security measures and safeguard sensitive information effectively. Stay ahead of the curve with Thycotic Secret Server for a robust and secure enterprise environment.