Advanced FreeRADIUS Security Configurations for Enterprise Networks sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail and brimming with originality from the outset.
In this article, we delve into the critical aspects of enhancing network security through advanced configurations in FreeRADIUS, shedding light on its significance and practical applications.
Overview of FreeRADIUS Security Configurations
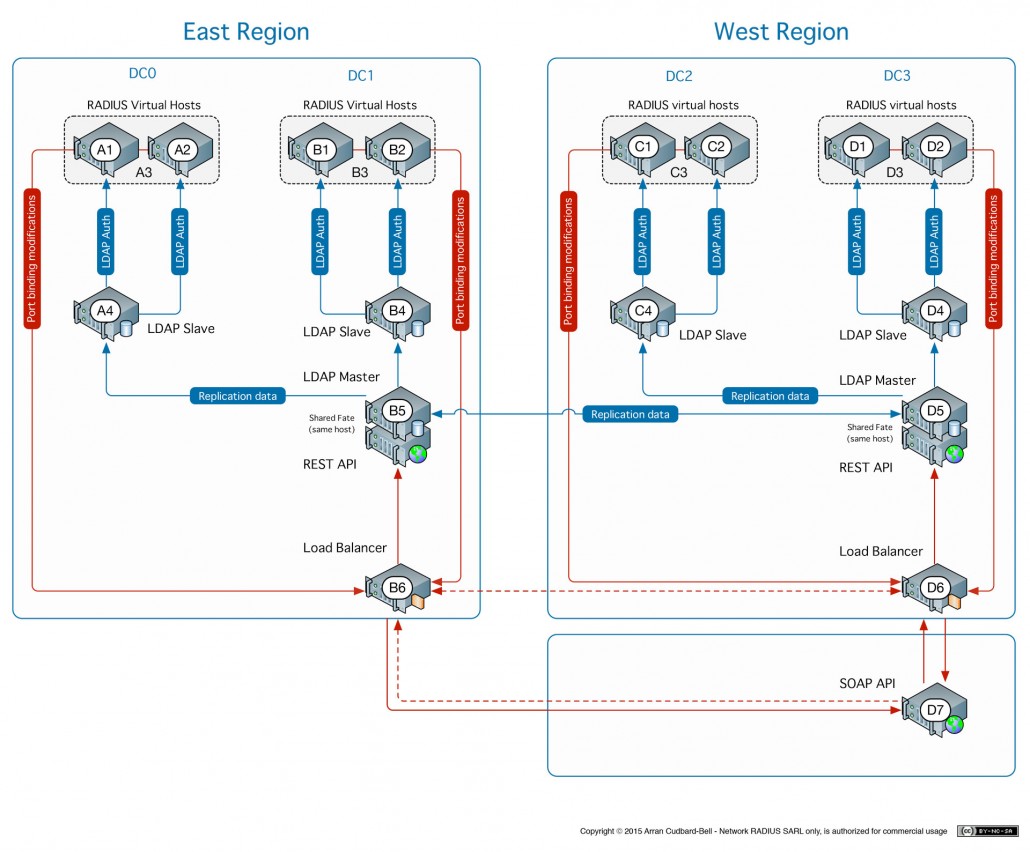
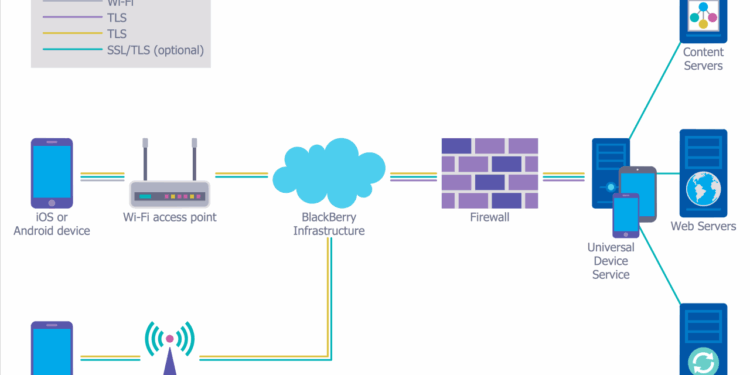
Implementing advanced security configurations in enterprise networks using FreeRADIUS is crucial in safeguarding sensitive data and ensuring network integrity. FreeRADIUS plays a key role in network security by providing authentication, authorization, and accounting (AAA) services, making it a critical component in controlling access to resources.
Advanced security configurations are necessary to enhance the overall security posture of enterprise networks. By fine-tuning settings and implementing additional security measures within FreeRADIUS, organizations can better protect against various cyber threats and unauthorized access attempts.
Importance of FreeRADIUS Security Configurations
- Secure Authentication: FreeRADIUS helps in verifying the identity of users and devices before granting access to network resources, reducing the risk of unauthorized access.
- Access Control: Advanced configurations enable granular control over user privileges and permissions, ensuring that only authorized users can access specific resources.
- Data Protection: By encrypting data transmissions and enforcing secure communication protocols, FreeRADIUS helps in safeguarding sensitive information from interception or tampering.
Examples of Security Threats Mitigated by FreeRADIUS
- Brute Force Attacks: FreeRADIUS can detect and mitigate brute force attacks by implementing account lockout policies and rate-limiting mechanisms to prevent unauthorized login attempts.
- Identity Spoofing: Advanced security configurations in FreeRADIUS can detect and prevent identity spoofing attacks, ensuring that only legitimate users are granted access to the network.
- Eavesdropping: By using encryption protocols like EAP-TLS or PEAP, FreeRADIUS can protect against eavesdropping attacks, securing data in transit between clients and servers.
Implementing Two-Factor Authentication with FreeRADIUS
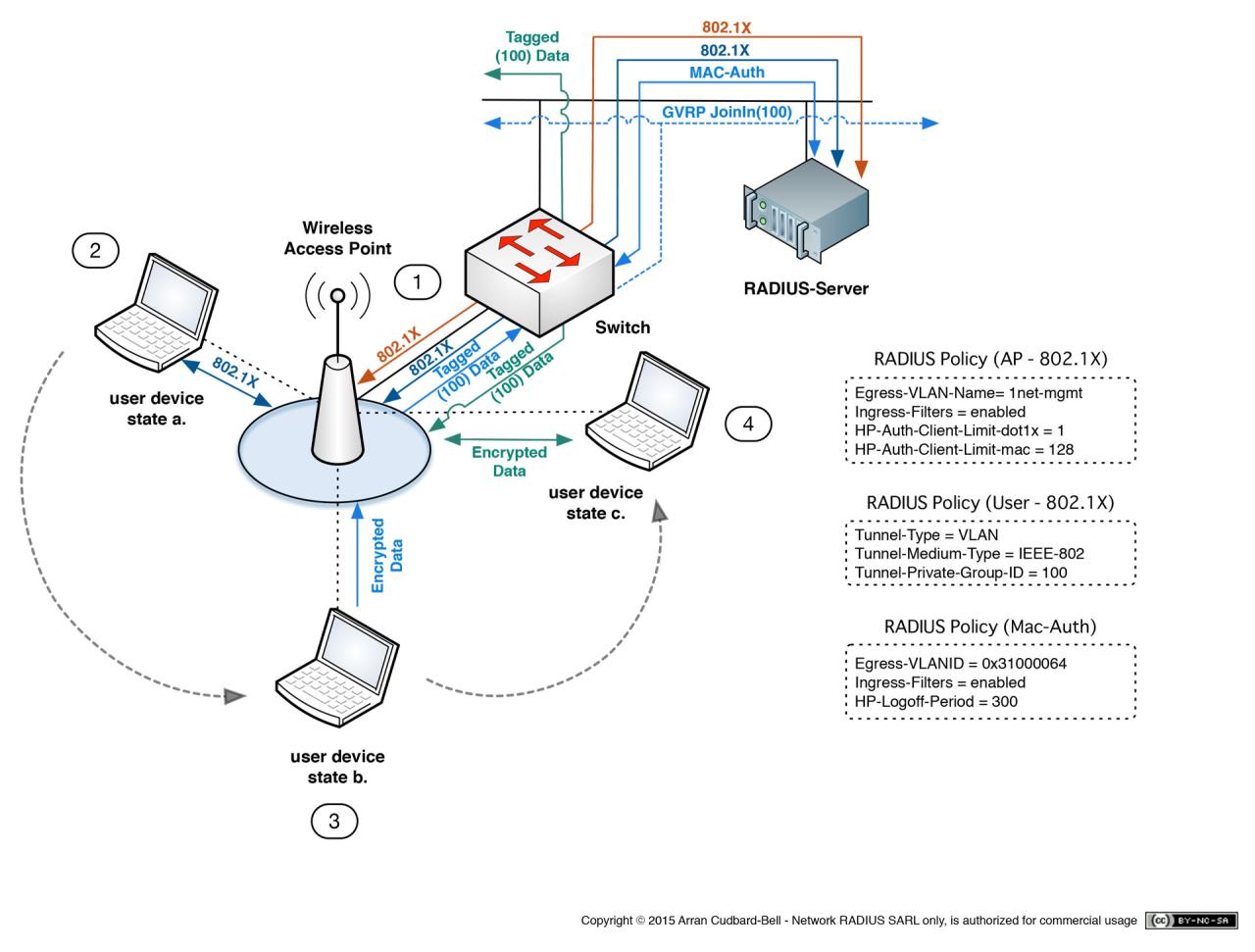
Two-factor authentication is a security process that requires two forms of identification in order to grant access to a system or network. This enhances security by adding an extra layer of protection beyond just a password.
FreeRADIUS can be configured to support two-factor authentication for enterprise networks by integrating with various authentication methods such as Google Authenticator, YubiKey, or SMS verification codes.
Setting up Two-Factor Authentication in FreeRADIUS
- Install and configure the FreeRADIUS server on your network.
- Choose a two-factor authentication method to integrate with FreeRADIUS, such as Google Authenticator.
- Configure the FreeRADIUS server to support the chosen authentication method by updating the configuration files.
- Generate and distribute authentication tokens or keys to the users who will be accessing the network.
- Test the two-factor authentication setup by attempting to log in with the additional authentication method.
Hardening FreeRADIUS Server Security
When it comes to securing a FreeRADIUS server, implementing best practices is crucial to protect against potential vulnerabilities. By hardening the security of the server, you can enhance its overall security posture and prevent unauthorized access or attacks.
Implementing Firewall Rules
- Utilize firewall rules to control incoming and outgoing traffic to the FreeRADIUS server.
- Restrict access to only necessary ports and protocols, such as UDP port 1812 for RADIUS authentication.
- Regularly review and update firewall rules to adapt to changing security requirements.
Enforcing Strong Password Policies
- Require users to use complex passwords containing a mix of letters, numbers, and special characters.
- Enforce password expiration and regular password changes to minimize the risk of credential compromise.
- Implement multi-factor authentication to add an extra layer of security beyond passwords.
Regular Software Updates
- Keep the FreeRADIUS server software up to date with the latest security patches and updates.
- Regularly check for security advisories and apply patches promptly to mitigate known vulnerabilities.
- Consider setting up automatic updates to ensure timely patching of security flaws.
Logging and Monitoring
- Enable logging to track and monitor all activities on the FreeRADIUS server, including authentication attempts and access logs.
- Implement real-time monitoring tools to detect suspicious behavior or unauthorized access attempts.
- Regularly review logs and monitor alerts for any signs of security incidents or breaches.
Integrating FreeRADIUS with Network Access Control (NAC) Systems
Integrating FreeRADIUS with Network Access Control (NAC) systems can significantly enhance network security by providing a centralized approach to authentication, authorization, and accounting.
Benefits of Integrating FreeRADIUS with NAC Systems
- Improved Network Security: By integrating FreeRADIUS with NAC systems, organizations can ensure that only authorized users and devices have access to the network, reducing the risk of unauthorized access.
- Enhanced Visibility: The integration allows for better visibility into network traffic, enabling administrators to monitor and analyze user behavior more effectively.
- Controlled Access: NAC systems coupled with FreeRADIUS provide granular control over network access, allowing administrators to enforce policies based on user identity, device type, and other factors.
Process of Integrating FreeRADIUS with Popular NAC Solutions
- Choose a Compatible NAC Solution: Select a NAC solution that is compatible with FreeRADIUS, ensuring seamless integration and interoperability.
- Configure FreeRADIUS Attributes: Define the necessary attributes within FreeRADIUS to communicate with the chosen NAC solution, such as RADIUS attributes for authorization and accounting.
- Implement NAC Policies: Set up NAC policies within the chosen solution to enforce access control based on the information provided by FreeRADIUS during the authentication process.
- Test and Monitor: Thoroughly test the integration to ensure that it functions as intended, and monitor network activity to identify any issues or anomalies.
Enhanced Security Enforcement with FreeRADIUS-NAC Integration
Integrating FreeRADIUS with NAC systems enhances security enforcement within the network by:
Enabling dynamic access control based on user identity and device posture.
Providing real-time visibility into network access and usage.
Automating security policy enforcement to respond swiftly to security threats.
Last Recap
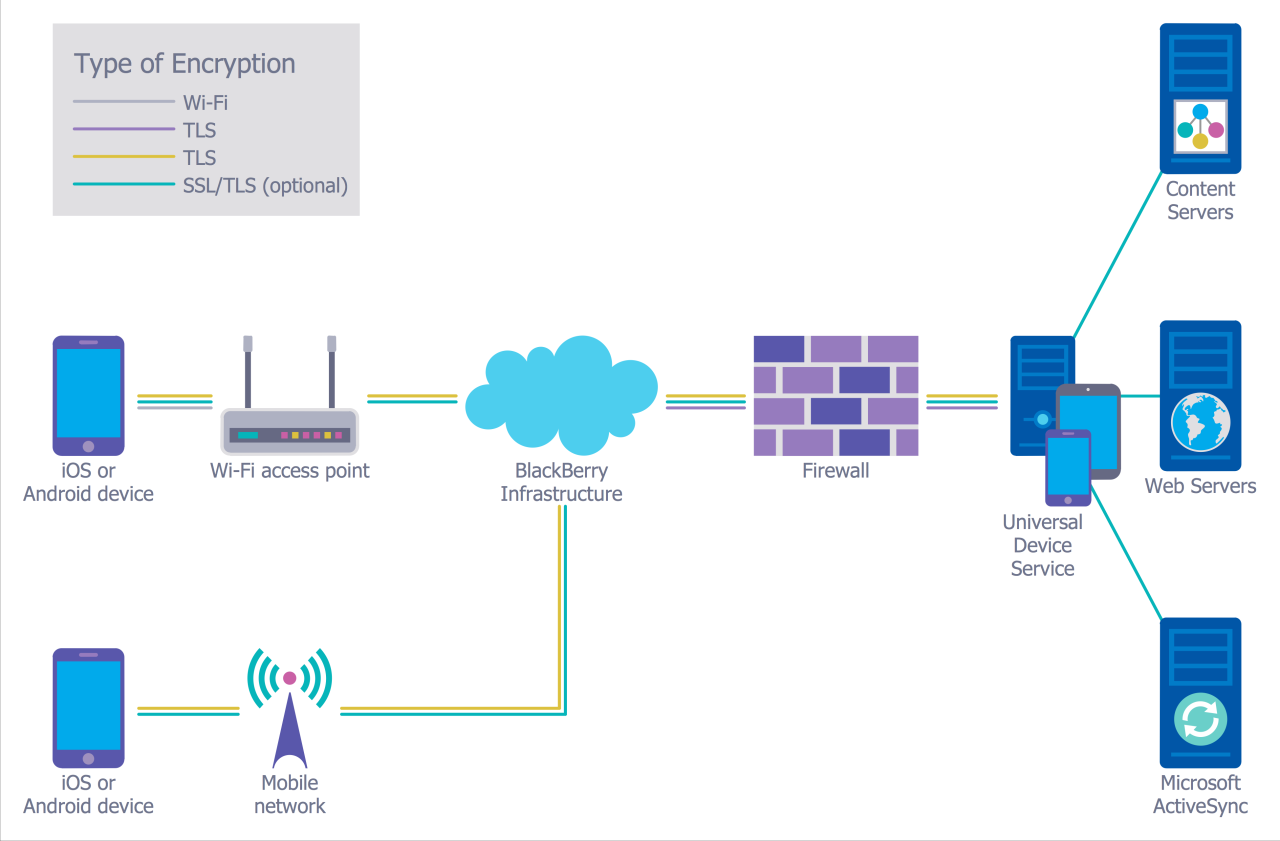
As we conclude our exploration of Advanced FreeRADIUS Security Configurations for Enterprise Networks, it becomes evident that the proactive approach to network security is paramount in today's digital landscape. Implementing these strategies can undoubtedly fortify your network against potential threats and vulnerabilities, ensuring a robust defense mechanism for your enterprise.