Embark on a journey through the realm of Privileged Access Management (PAM) with a focus on the best practices for utilizing Secret Server. This guide promises to enlighten you on the crucial aspects of securing sensitive data and optimizing access controls.
Delve into the world of Secret Server as we explore its pivotal role in fortifying cybersecurity measures and ensuring a robust defense against potential threats.
Introduction to Secret Server in Privileged Access Management (PAM)
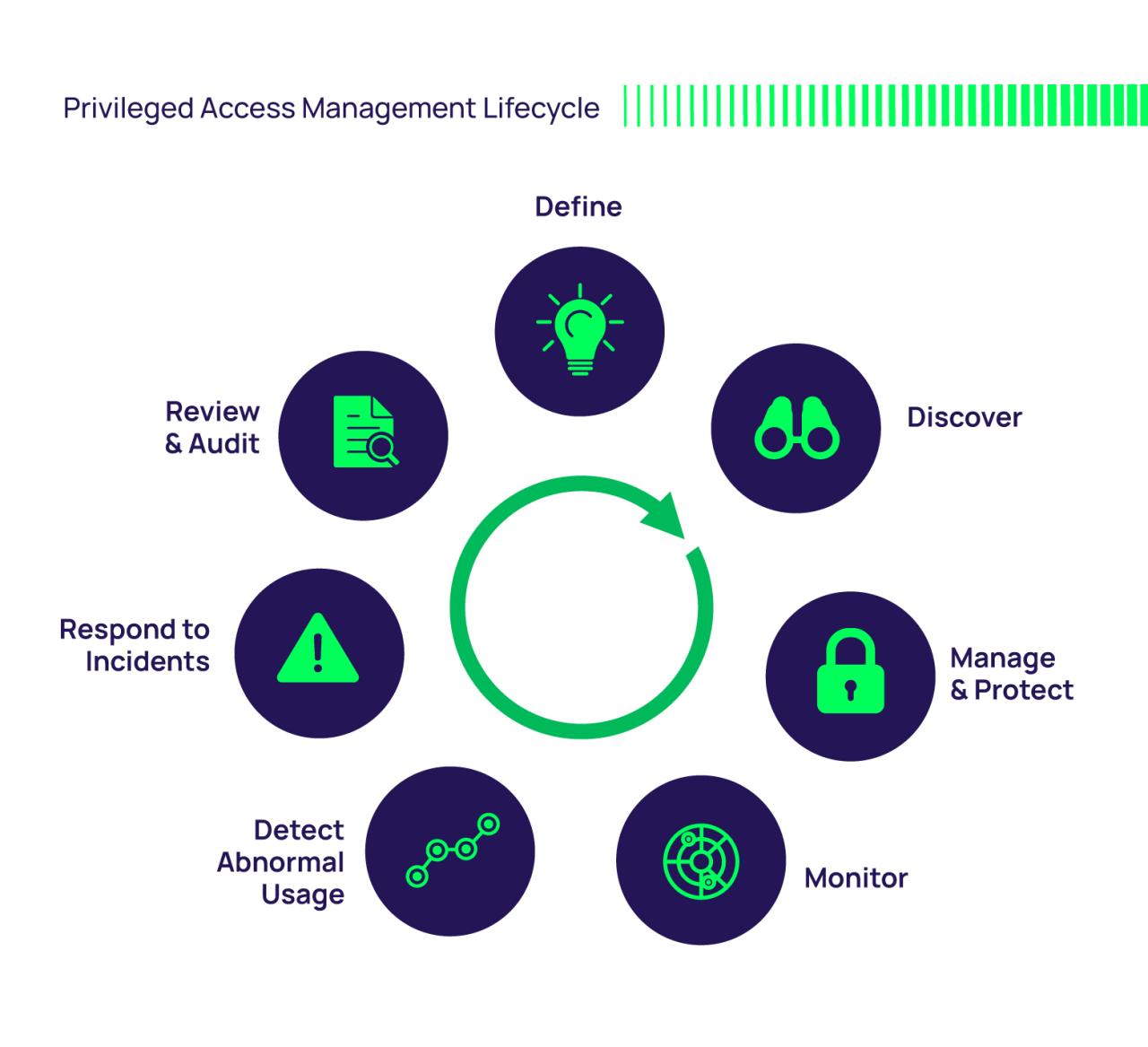
Privileged Access Management (PAM) is a crucial aspect of cybersecurity that focuses on securing and managing privileged accounts within an organization. These accounts have elevated permissions and access to sensitive data, making them prime targets for cyber threats.Secret Server is a PAM solution that helps organizations securely store, manage, and monitor privileged account credentials.
It acts as a centralized repository for passwords, SSH keys, and other sensitive information, ensuring that access is tightly controlled and audited.Implementing PAM solutions like Secret Server is essential for enhancing security posture and protecting against insider threats, external attacks, and data breaches.
By enforcing least privilege access and implementing robust security controls, organizations can reduce the risk of unauthorized access and ensure compliance with regulatory requirements.
Key Features of Secret Server for PAM

Secret Server offers a range of key features that are essential for effective privileged access management (PAM). These features help organizations secure sensitive information and streamline access control processes through automation.
Centralized Password Management
Secret Server provides a centralized platform for storing and managing privileged account credentials, ensuring that sensitive information is securely stored and easily accessible only to authorized users. This centralization helps organizations enforce strong password policies and monitor access to critical systems.
Role-Based Access Control
With Secret Server, administrators can define granular access controls based on roles and responsibilities, ensuring that users only have access to the resources they need to perform their job functions. This feature helps minimize the risk of unauthorized access and data breaches.
Audit Trail and Reporting
Secret Server offers robust auditing capabilities that track all access and activities related to privileged accounts. This audit trail helps organizations meet compliance requirements and investigate security incidents by providing detailed reports on user activities and changes made to sensitive information.
Automated Password Rotation
Automation plays a crucial role in Secret Server by enabling organizations to automatically rotate passwords for privileged accounts at regular intervals. This feature helps reduce the risk of credential theft and ensures that passwords are regularly updated without manual intervention.
Session Monitoring and Recording
Secret Server allows administrators to monitor and record privileged sessions in real-time, providing visibility into user activities and enabling quick response to any suspicious behavior. This feature helps organizations detect and mitigate security threats before they escalate.
Integration Capabilities
Secret Server offers seamless integration with other security tools and systems, allowing organizations to extend the functionality of the platform and enhance their overall security posture. This integration capability enables organizations to leverage existing investments in security technologies and streamline their PAM processes.
Implementation Best Practices for Secret Server
When setting up Secret Server for Privileged Access Management (PAM), it is crucial to follow best practices to ensure maximum security and efficiency. Below are some key steps and tips to consider:
Step-by-Step Guide for Setting Up Secret Server
- Start by installing Secret Server on a dedicated server to ensure isolation and security.
- Create separate user accounts with unique privileges for administrators and end-users to limit access.
- Implement strong password policies and enable multi-factor authentication to enhance security.
- Regularly update and patch Secret Server to address any vulnerabilities and ensure the latest security features are in place.
Tips for Configuring Secret Server for Maximum Security
- Utilize role-based access control to assign permissions based on job roles and responsibilities.
- Encrypt sensitive data stored in Secret Server to protect it from unauthorized access.
- Enable auditing and monitoring features to track user activities and detect any suspicious behavior.
- Set up automated password rotation to minimize the risk of compromised credentials.
Integration Options with Other Security Tools
- Integrate Secret Server with SIEM solutions to centralize log data and improve threat detection capabilities.
- Connect Secret Server with privileged session management tools to monitor and control privileged access in real-time.
- Implement API integrations with identity and access management systems for seamless user provisioning and deprovisioning.
- Explore integrations with threat intelligence platforms to enhance threat visibility and response capabilities.
Security Measures and Compliance with Secret Server

Secret Server plays a crucial role in enhancing security controls for privileged accounts by providing a centralized platform for managing and securing sensitive information.
Enhanced Security Controls
- Secret Server offers encrypted storage for passwords and other confidential data, ensuring that only authorized users can access this information.
- Multi-factor authentication capabilities add an extra layer of security to prevent unauthorized access to privileged accounts.
- Role-based access control allows administrators to define and enforce access policies based on job responsibilities, minimizing the risk of misuse.
Compliance Requirements Assistance
- Secret Server assists organizations in meeting compliance requirements by providing detailed audit trails and reports on privileged account activities.
- Integration with compliance frameworks such as PCI DSS and HIPAA ensures that security controls align with industry standards and regulations.
- Automated password rotation and expiration policies help maintain compliance with password management best practices.
Importance of Audits and Monitoring
Regular audits and monitoring are essential components of a robust privileged access management strategy when using Secret Server.
- Continuous monitoring of privileged account activities can help detect any suspicious behavior or unauthorized access attempts promptly.
- Audits provide insights into who accessed what information, when, and why, aiding in incident response and compliance reporting.
- Proactive monitoring and regular audits ensure that security policies are being followed and help identify areas for improvement in the access management process.
Training and User Adoption for Secret Server
Training users on how to effectively use Secret Server is crucial for successful implementation and utilization of the platform within an organization. Here are some tips to ensure user adoption and buy-in for Secret Server, along with the role of ongoing education and awareness in maintaining a secure PAM environment.
Designing a Training Program
- Develop a customized training program based on the specific needs and roles of users within the organization.
- Include hands-on training sessions to familiarize users with the features and functionalities of Secret Server.
- Provide clear documentation and resources for users to reference after the training sessions.
Ensuring User Adoption and Buy-In
- Highlight the benefits of using Secret Server, such as enhanced security, streamlined access management, and improved compliance.
- Engage key stakeholders and influencers within the organization to advocate for the use of Secret Server.
- Encourage feedback from users to address any concerns or challenges they may face during the adoption process.
Role of Ongoing Education and Awareness
- Provide regular updates and training sessions to keep users informed about new features, best practices, and security protocols.
- Implement a communication strategy to raise awareness about the importance of secure access management and the role of Secret Server in maintaining a secure environment.
- Conduct periodic security awareness training to educate users about potential threats and the impact of PAM on overall cybersecurity.
Final Review
As we conclude our exploration of Best Practices for Using Secret Server in Privileged Access Management (PAM), it becomes evident that a proactive approach to security is paramount in safeguarding critical assets. Implementing these practices not only enhances protection but also fosters a culture of resilience within organizations.