Edge Server Deployment Techniques for Maximizing Network Performance sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail with casual formal language style and brimming with originality from the outset.
The topic delves into the intricacies of optimizing network performance through edge server deployment, shedding light on the best practices and strategies to enhance efficiency and speed in today's digital landscape.
Edge Server Basics
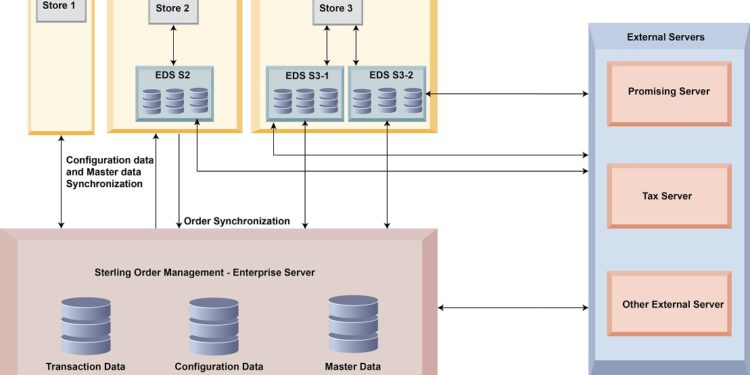
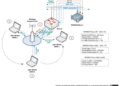
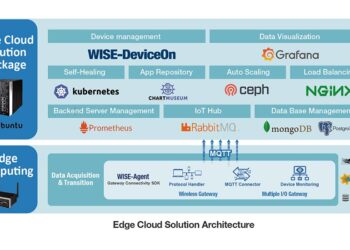
Edge servers play a crucial role in network architecture by serving as intermediary devices between clients and origin servers. These servers are strategically placed at the edge of a network to improve content delivery and optimize performance.Edge servers can be deployed in various scenarios to enhance network efficiency.
For example, in a Content Delivery Network (CDN), edge servers are distributed geographically to reduce latency and deliver content faster to users. Additionally, edge servers can be used in load balancing scenarios to distribute incoming traffic across multiple servers, ensuring optimal performance and reliability.The benefits of using edge servers for network performance optimization are significant.
By caching content closer to end-users, edge servers reduce the distance data needs to travel, resulting in faster load times and improved user experience. Moreover, edge servers can help offload traffic from origin servers, reducing the risk of overload and downtime during peak usage periods.
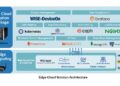
Techniques for Efficient Edge Server Deployment
Deploying edge servers efficiently is crucial for maximizing network performance. By utilizing best practices and various deployment techniques such as caching, load balancing, and content delivery networks, organizations can significantly improve latency and reduce data transfer times.
Cache Optimization
One of the key techniques for efficient edge server deployment is cache optimization. By caching frequently accessed content closer to end-users, edge servers can reduce the load on origin servers and deliver content faster to users. This technique helps improve overall network performance by minimizing latency and reducing data transfer times.
Load Balancing
Another important deployment technique is load balancing, which involves distributing incoming network traffic across multiple edge servers. This helps prevent any single server from being overwhelmed and ensures optimal performance even during high traffic periods. By effectively balancing the workload, organizations can enhance network efficiency and reliability.
Content Delivery Networks (CDNs)
Implementing a Content Delivery Network (CDN) is also a valuable technique for efficient edge server deployment. CDNs use a network of distributed edge servers to deliver content to users based on their geographic location. By serving content from the nearest edge server, CDNs can significantly reduce latency and improve data transfer speeds, ultimately enhancing the overall user experience.
Network Performance Optimization Strategies
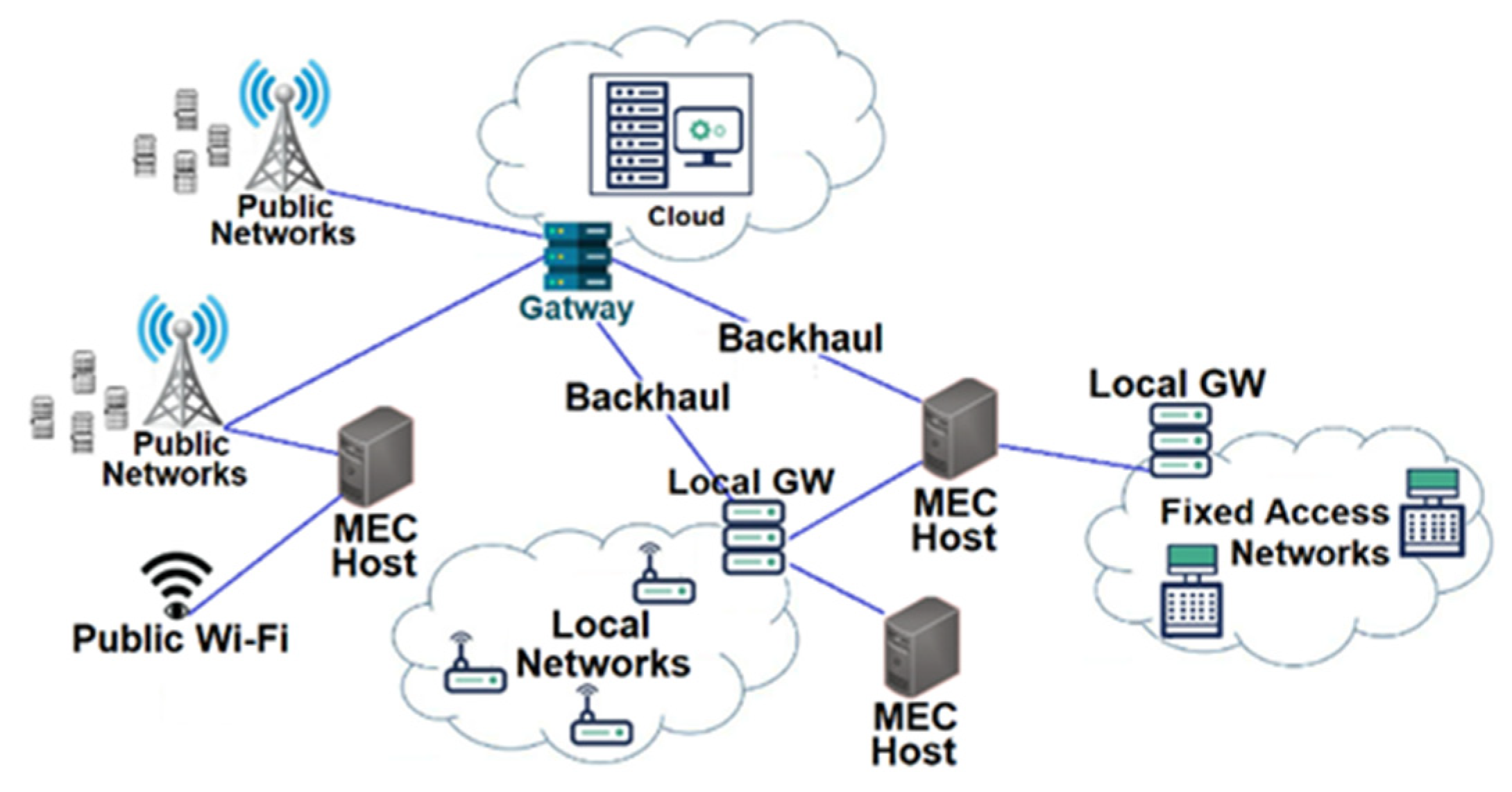
When it comes to optimizing network performance through edge server deployment, there are several strategies that can be implemented to enhance data processing speeds and improve user experiences.
Leveraging Edge Computing for Faster Data Processing
- Utilizing edge servers to process data closer to the end-users helps reduce latency and speeds up the delivery of content.
- By distributing computing resources to the edge of the network, data can be processed more efficiently, leading to faster response times.
- Edge computing allows for real-time data analysis and decision-making, enabling quicker actions to be taken based on the processed information.
Improved User Experiences through Edge Server Deployment
- Edge servers can cache content closer to users, reducing the time it takes to retrieve information and enhancing overall user experience.
- With edge computing, applications can run smoother and faster, providing a seamless experience for end-users.
- By reducing network congestion and optimizing data delivery, edge servers can ensure a more reliable and consistent user experience.
Successful Network Performance Optimization Examples
- Content Delivery Networks (CDNs) use edge servers to cache and deliver content efficiently, resulting in faster loading times for websites and applications.
- Video streaming platforms leverage edge computing to deliver high-quality video content with minimal buffering, enhancing user satisfaction.
- Online gaming companies deploy edge servers to reduce latency and provide a smooth gaming experience for players around the world.
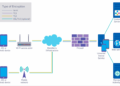
Security Considerations in Edge Server Deployment
When deploying edge servers, it is crucial to consider the security implications to protect sensitive data and ensure network integrity. Here, we will discuss potential security risks, measures to safeguard edge servers from cyber threats, and ways to maintain data confidentiality and integrity.
Potential Security Risks
- Unauthorized access: Hackers may attempt to gain access to edge servers to steal data or disrupt operations.
- Denial of Service (DoS) attacks: Attackers can overwhelm edge servers with traffic, causing service disruptions.
- Data breaches: Sensitive information stored on edge servers could be compromised if not properly secured.
Security Measures for Protection
- Implement encryption: Encrypting data in transit and at rest can prevent unauthorized access and data breaches.
- Use firewalls and intrusion detection systems: Setting up firewalls and IDS can help detect and block malicious traffic.
- Regular security audits: Conducting routine security assessments can identify vulnerabilities and address them promptly.
Ensuring Data Integrity and Confidentiality
- Access control mechanisms: Limiting access to edge servers to authorized personnel can help maintain data confidentiality.
- Secure communication protocols: Using secure protocols like HTTPS can ensure data integrity during transmission.
- Data backup and recovery: Regularly backing up data stored on edge servers can help prevent data loss due to security incidents.
Closing Notes

In conclusion, Edge Server Deployment Techniques for Maximizing Network Performance encapsulates the essence of leveraging cutting-edge technologies to elevate network efficiency and user experiences. The discussion unveils the importance of strategic deployment and optimization in achieving seamless connectivity and performance in the digital realm.