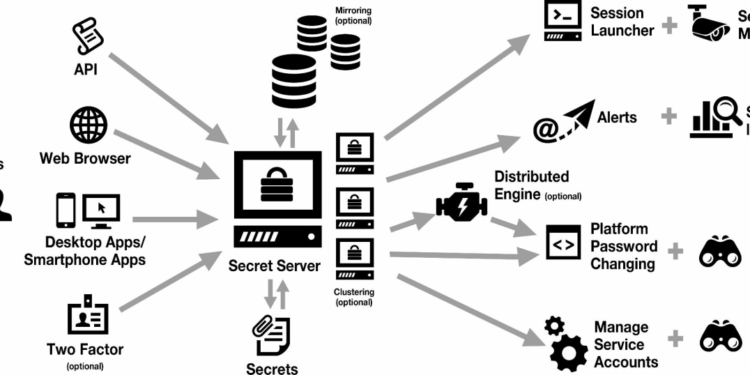
Embark on a journey through the intricacies of Enterprise-Level Thycotic Secret Server Integration and Best Practices. This topic delves into the significance of integrating Thycotic Secret Server at an enterprise level, the advantages of a centralized system for managing privileged accounts, and the essential role it plays in various industries.
The subsequent paragraphs will offer detailed insights into setting up Thycotic Secret Server, overcoming implementation challenges, understanding security measures, compliance considerations, scalability, and performance optimization.
Overview of Enterprise-Level Thycotic Secret Server Integration
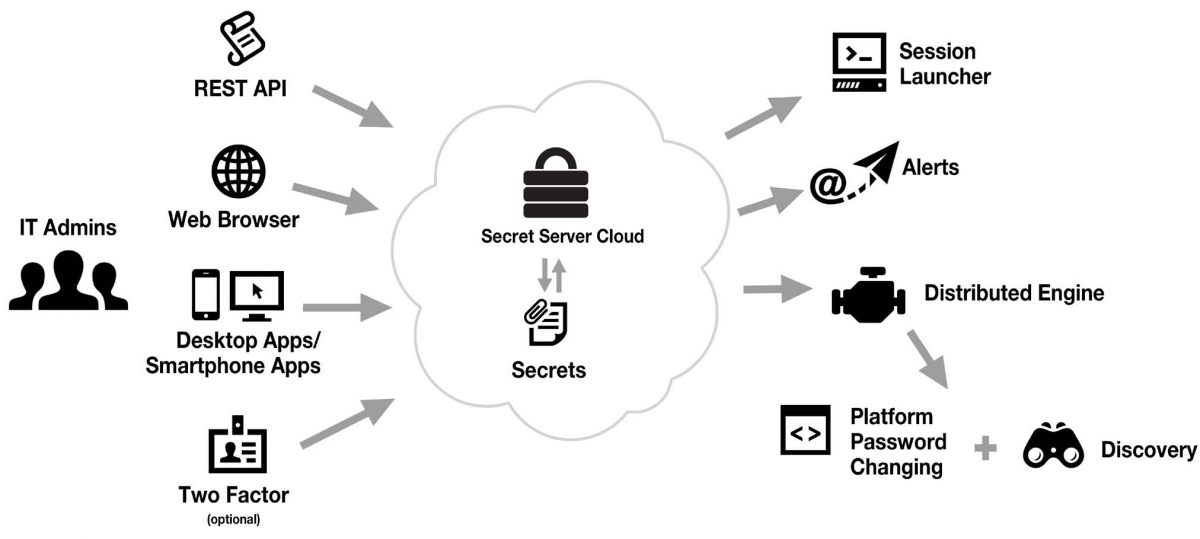
Integrating Thycotic Secret Server at the enterprise level is crucial for organizations looking to enhance their security measures and streamline privileged account management. By centralizing the management of sensitive information, businesses can ensure better control, compliance, and overall security posture.
Importance of Integration
- Enhanced Security: Centralizing privileged account management reduces the risk of unauthorized access and data breaches.
- Improved Compliance: Having a centralized system helps in meeting regulatory requirements and audit standards more effectively.
- Efficient Operations: Streamlining access to critical systems and applications simplifies IT operations and enhances productivity.
Benefits of Centralized System
- Reduced Complexity: Managing privileged accounts from a single platform eliminates the need for multiple tools and processes.
- Enhanced Visibility: Organizations gain better visibility into who has access to what systems, enabling proactive monitoring and response.
- Risk Mitigation: By enforcing strict access controls and monitoring activities, the risk of insider threats or data leaks is minimized.
Crucial Industries for Integration
- Finance: Financial institutions handle sensitive customer data and transactions, making secure privileged account management essential.
- Healthcare: Healthcare organizations store confidential patient information that requires strict access controls to protect privacy.
- Government: Government agencies deal with classified data and national security information, necessitating robust security measures.
Best Practices for Implementing Thycotic Secret Server
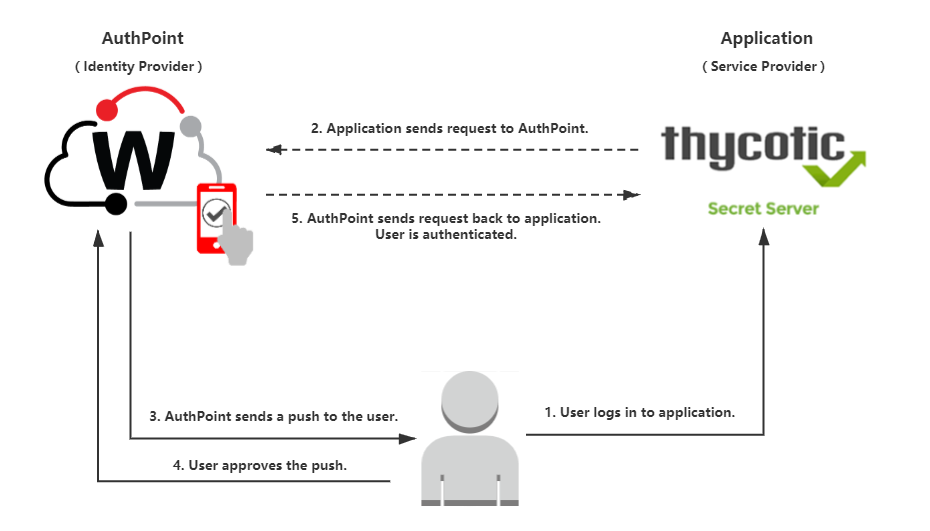
When setting up Thycotic Secret Server for enterprise-level use, it is essential to follow best practices to ensure smooth implementation and optimal performance. Below are some key steps, challenges, and tips for IT administrators to consider during the process.
Setting Up Thycotic Secret Server
- Ensure thorough planning before deployment to define user roles, access controls, and security policies.
- Properly configure user permissions and define who can access, view, and modify sensitive information stored in the Secret Server.
- Integrate Active Directory or LDAP for seamless user authentication and centralized management of user accounts.
- Regularly back up the Secret Server database to prevent data loss in case of system failures or cyber attacks.
Common Challenges and Solutions
- Challenge: Resistance to change from users accustomed to traditional password management systems.
- Overcome this by providing comprehensive training and support to help users transition smoothly.
- Challenge: Ensuring compliance with industry regulations and data protection standards.
- Address this by regularly auditing access logs, enforcing strong password policies, and conducting security assessments.
- Challenge: Managing a large number of secrets and credentials efficiently.
- Implement folder structures, naming conventions, and access controls to organize and secure secrets effectively.
Role of IT Administrators
- IT administrators play a crucial role in maintaining and optimizing Thycotic Secret Server by regularly updating the software, monitoring system performance, and resolving any technical issues promptly.
- They are responsible for training users, enforcing security policies, and ensuring that the Secret Server aligns with the organization's security objectives and compliance requirements.
- Collaboration with other IT teams and stakeholders is essential to ensure the successful integration and continuous improvement of the Secret Server system.
Security Measures and Compliance Considerations
When integrating Thycotic Secret Server at the enterprise level, it is crucial to consider the security features that make it suitable for such implementations, as well as compliance requirements that need to be met.
Security Features of Thycotic Secret Server
- Role-based access control: Thycotic Secret Server allows administrators to define granular access controls based on roles, ensuring that only authorized users can access sensitive information.
- Encryption: All data stored in Thycotic Secret Server is encrypted, both at rest and in transit, providing an added layer of security against unauthorized access.
- Audit trails: Thycotic Secret Server logs all access and changes made to secrets, providing a detailed audit trail that can help track any unauthorized activities.
Compliance Considerations with Thycotic Secret Server
- GDPR: Thycotic Secret Server helps organizations comply with GDPR by ensuring that access to personal data is restricted to authorized personnel only, thus reducing the risk of data breaches.
- HIPAA: Thycotic Secret Server aids in meeting HIPAA requirements by enforcing strong access controls and encryption measures to protect sensitive patient information.
- SOX: Thycotic Secret Server assists in complying with SOX regulations by providing detailed audit trails and access controls to monitor and track changes to financial data.
Examples of Security Breaches without Proper Implementation
Without proper implementation and adherence to compliance standards, organizations are at risk of facing security breaches that could have severe consequences. For instance, unauthorized access to sensitive data, data leaks, and compromised credentials are some of the potential risks that could lead to financial losses, reputational damage, and legal consequences.
Scalability and Performance Optimization
When it comes to scaling Thycotic Secret Server for a growing enterprise, it's crucial to have a solid strategy in place to ensure optimal performance. By implementing best practices and continuously monitoring and maintaining performance levels, you can effectively meet the increasing demands of your organization.
Strategies for Scaling Thycotic Secret Server
- Utilize load balancing techniques to distribute traffic evenly across multiple servers, ensuring efficient use of resources.
- Implement a scalable infrastructure that can easily accommodate the addition of new servers or resources as needed.
- Leverage virtualization technologies to dynamically allocate resources based on demand, optimizing performance and scalability.
Best Practices for Optimizing Performance
- Regularly review and optimize server configurations to ensure they meet the performance requirements of your organization.
- Utilize caching mechanisms to reduce the load on servers and improve response times for user requests.
- Monitor system performance metrics and analyze trends to proactively identify and address potential bottlenecks or issues.
Monitoring and Maintaining Performance Levels
- Set up automated monitoring tools to continuously track system performance and alert you to any deviations from normal operations.
- Establish regular performance reviews to assess the effectiveness of your optimization efforts and make adjustments as needed.
- Implement a robust maintenance schedule to ensure that servers are regularly updated, patched, and optimized for peak performance.
Concluding Remarks
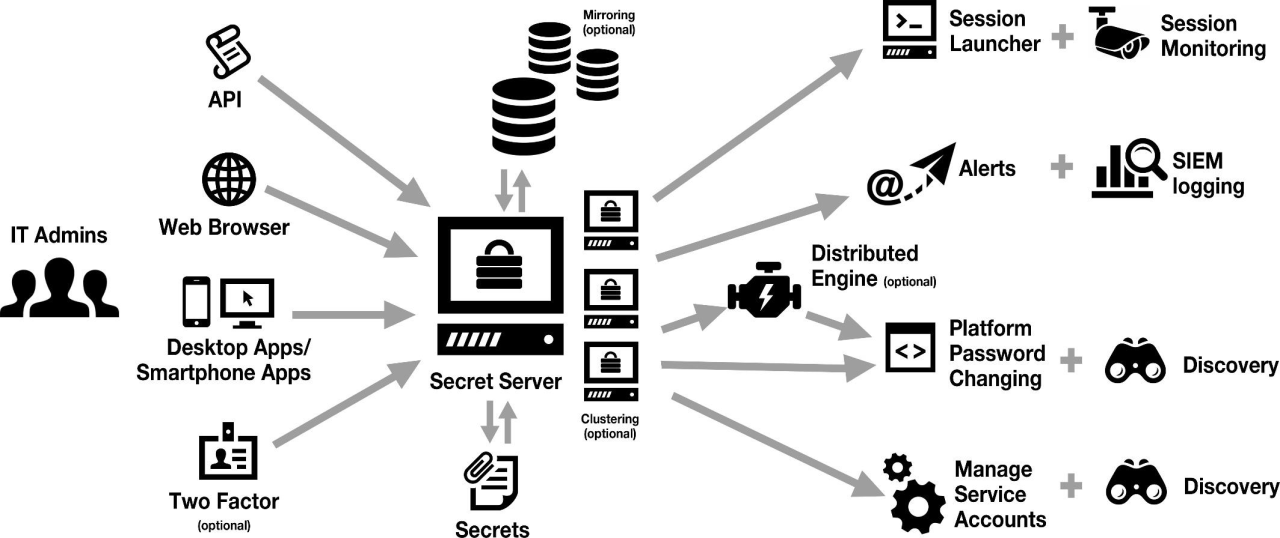
In conclusion, Enterprise-Level Thycotic Secret Server Integration and Best Practices are vital components in ensuring a secure and efficient system for managing privileged accounts. This guide has shed light on the key aspects to consider when implementing and maintaining Thycotic Secret Server at an enterprise level.