How to Secure Sensitive Credentials with Secret Server dives into the intricacies of safeguarding vital information, shedding light on the significance of protecting sensitive data in today's digital landscape. This guide offers a deep dive into the world of credential security, providing insights and best practices for ensuring the safety of valuable information.
The following sections will cover key aspects such as setting up Secret Server, integrating it with other tools for enhanced security, monitoring access, and disaster recovery planning.
Introduction to Securing Sensitive Credentials with Secret Server
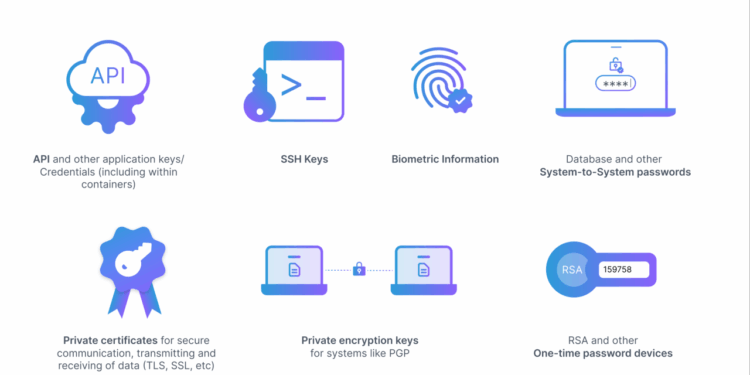
Sensitive credentials refer to confidential information such as passwords, API keys, and other access codes that grant users access to secure systems or data.
Securing sensitive credentials is crucial to protect sensitive data from unauthorized access, data breaches, and cyber attacks. Failure to secure these credentials can lead to severe consequences, including financial loss, reputational damage, and legal implications.
Role of Secret Server in Managing Sensitive Credentials
Secret Server is a privileged access management solution that helps organizations securely store, manage, and distribute sensitive credentials. It provides a centralized platform for storing and accessing passwords, API keys, and other confidential information, ensuring that only authorized users can access them.
Best Practices for Securing Sensitive Credentials
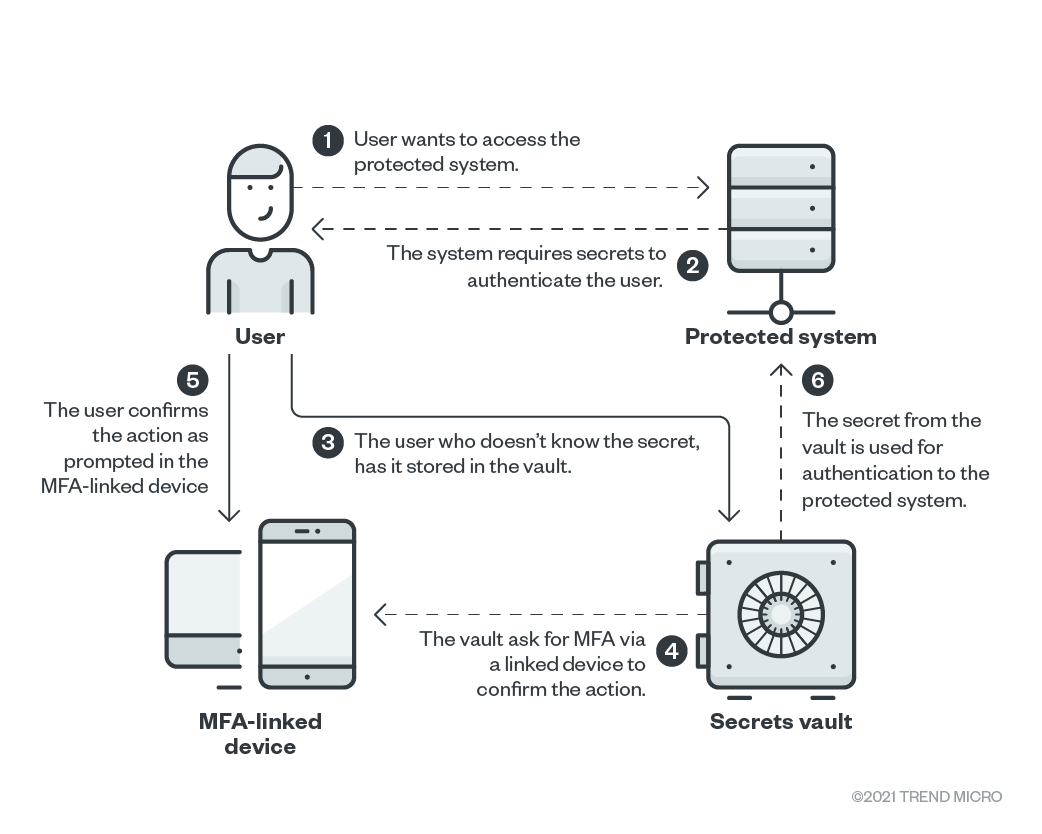
When it comes to securing sensitive credentials, there are several best practices that organizations should follow to ensure the safety of their data and systems. These practices help mitigate the risk of unauthorized access and potential breaches.
Encryption Methods for Protecting Credentials
One of the most effective ways to protect sensitive credentials is through encryption. By encrypting data, organizations can ensure that even if a breach occurs, the information stolen will be unreadable and unusable to unauthorized individuals.
- Use strong encryption algorithms such as AES (Advanced Encryption Standard) to safeguard sensitive information.
- Implement secure key management practices to protect encryption keys and prevent unauthorized access.
- Utilize secure communication protocols like SSL/TLS to encrypt data transmissions and prevent interception.
Principle of Least Privilege and Its Relevance to Credential Security
The principle of least privilege is a security concept that restricts users' access rights to only what is necessary to perform their job functions. When applied to credential security, this principle helps limit the exposure of sensitive information and reduces the risk of unauthorized access.
- Grant users the minimum level of access required to perform their tasks to prevent unauthorized access to sensitive credentials.
- Regularly review and update user permissions to align with their current job responsibilities and ensure they have access only to the necessary resources.
- Implement multi-factor authentication to add an extra layer of security and verify the identity of users before granting access to sensitive credentials.
Setting Up Secret Server for Credential Protection
When it comes to protecting sensitive credentials, setting up Secret Server is a crucial step in ensuring the security of your organization's data. By properly configuring this tool, you can effectively manage and safeguard important information.
Creating Secure Credential Entries within Secret Server
To create secure credential entries within Secret Server, follow these steps:
- Log in to Secret Server with your credentials.
- Click on the "Add" button to create a new entry.
- Enter the necessary details for the credential, such as the username and password.
- Ensure you assign the appropriate permissions to control who can access this information.
- Save the entry and make sure to regularly update the credentials for security purposes.
Configuring Access Controls in Secret Server
Configuring access controls in Secret Server is essential for maintaining the confidentiality of sensitive credentials. Here are some options to consider:
- Implement role-based access control to restrict access based on user roles.
- Utilize two-factor authentication for an added layer of security.
- Set up approval workflows to ensure that access to critical credentials is authorized.
- Audit user activity to monitor who is accessing sensitive information.
Integrating Secret Server with Other Tools for Enhanced Security
Integrating Secret Server with other security tools can significantly enhance the overall security posture of an organization. By combining the capabilities of Secret Server with other tools, organizations can create a robust security ecosystem that protects sensitive credentials effectively.
Benefits of Integrating Secret Server with Other Tools
- Improved Security Posture: Integrating Secret Server with other tools such as SIEM solutions or endpoint protection platforms can provide a layered approach to security, making it harder for unauthorized users to access sensitive credentials.
- Centralized Management: Integration with other tools allows for centralized management of security policies and access controls, streamlining security operations and ensuring consistency across the organization.
- Automated Workflows: Integration can enable automated workflows for tasks such as credential rotation, password resets, and access provisioning, reducing the burden on IT teams and minimizing the risk of human error.
Examples of Tools that can be Integrated with Secret Server
- Security Information and Event Management (SIEM) Solutions: Tools like Splunk or QRadar can be integrated with Secret Server to provide real-time monitoring and alerting for any suspicious activities related to sensitive credentials.
- Vulnerability Management Platforms: Integrating with tools like Nessus or Qualys can help identify and remediate vulnerabilities that may pose a risk to sensitive credentials stored in Secret Server.
- Identity and Access Management (IAM) Systems: Integration with IAM solutions like Active Directory or Okta can ensure seamless user authentication and access control for Secret Server, enhancing overall security.
Process of Integrating Secret Server with Third-Party Applications
Integrating Secret Server with third-party applications typically involves configuring APIs or connectors provided by both Secret Server and the respective tool. This process may vary depending on the tool being integrated, but generally, it requires setting up authentication, establishing secure communication channels, and mapping data fields between the systems.
Monitoring and Auditing Credential Access in Secret Server
Monitoring and auditing access to sensitive credentials is crucial for maintaining the security of an organization's data. By keeping track of who accesses which credentials and when, organizations can detect unauthorized access attempts and take immediate action to prevent potential security breaches.
Features for Tracking Credential Access in Secret Server
- Secret Server provides detailed logs that record all access to sensitive credentials, including user information and timestamps.
- Administrators can view a complete audit trail of all actions taken within Secret Server, allowing for easy monitoring of credential access.
- Secret Server offers customizable reporting options to generate specific reports on credential access for compliance and security purposes.
Setting Up Alerts for Unauthorized Access Attempts in Secret Server
- Configure alerts within Secret Server to notify administrators of any unauthorized access attempts or suspicious activities related to sensitive credentials.
- Define specific conditions for triggering alerts, such as multiple failed login attempts or access from unknown IP addresses, to proactively identify potential security threats.
- Integrate Secret Server with security information and event management (SIEM) systems to enhance alerting capabilities and centralize monitoring of credential access across the organization.
Disaster Recovery Planning for Sensitive Credentials
Disaster recovery planning for sensitive credentials is crucial to ensure the security and integrity of your organization's most valuable information. In the event of a data breach, system failure, or any other disaster, having a solid plan in place can mean the difference between a minor inconvenience and a major security breach.
Creating a Disaster Recovery Plan for Secret Server
When creating a disaster recovery plan for Secret Server, follow these steps to ensure that your sensitive credentials are protected:
- Identify Critical Credentials: Start by identifying the most critical credentials that need to be prioritized for backup and recovery.
- Define Backup Frequency: Determine how often backups of sensitive credentials should be taken to ensure minimal data loss in the event of a disaster.
- Choose Backup Locations: Select secure and geographically diverse backup locations to prevent a single point of failure.
- Establish Recovery Procedures: Develop detailed procedures for restoring sensitive credentials in case of a disaster, including who is responsible for executing the recovery process.
- Test the Plan Regularly: Regularly test the disaster recovery plan to ensure that it is effective and can be executed quickly and accurately when needed.
Backup and Restoration Procedures for Sensitive Credentials in Secret Server
When it comes to backup and restoration procedures for sensitive credentials in Secret Server, consider the following best practices:
- Regular Automated Backups: Set up automated backups of sensitive credentials to ensure that data is consistently backed up without manual intervention.
- Encryption of Backup Data: Encrypt backup data to protect sensitive credentials from unauthorized access during transit and storage.
- Secure Backup Storage: Store backup data in secure, off-site locations to prevent data loss in case of physical damage to the primary storage location.
- Version Control: Maintain a version history of backups to easily revert to a previous state in case of accidental deletion or corruption of sensitive credentials.
Final Thoughts
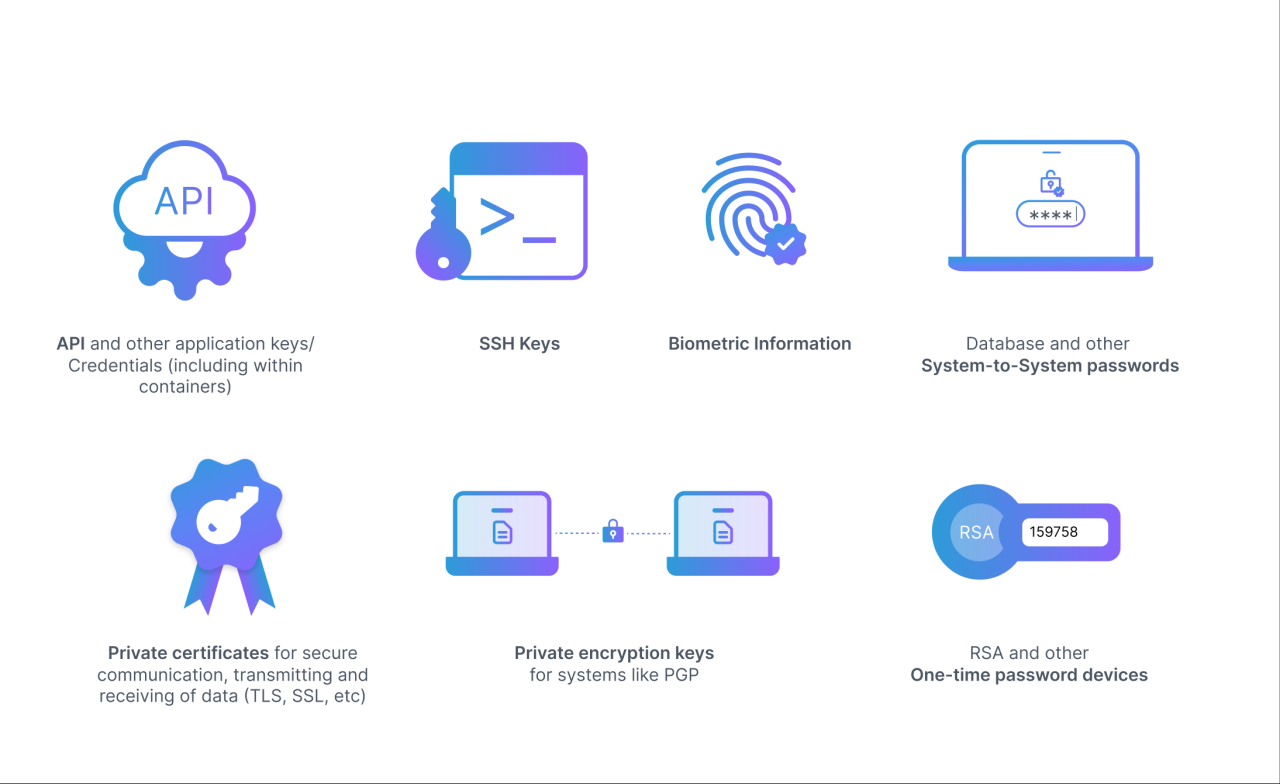
In conclusion, How to Secure Sensitive Credentials with Secret Server equips readers with the knowledge and tools necessary to fortify their data protection strategies. By implementing the best practices Artikeld in this guide, organizations can enhance their security posture and safeguard their sensitive credentials effectively.