Exploring the world of Thycotic Secret Server for enterprise security opens up a realm of possibilities. Dive into the setup process with us as we unravel the intricacies of securing sensitive data and optimizing performance.
Introduction to Thycotic Secret Server
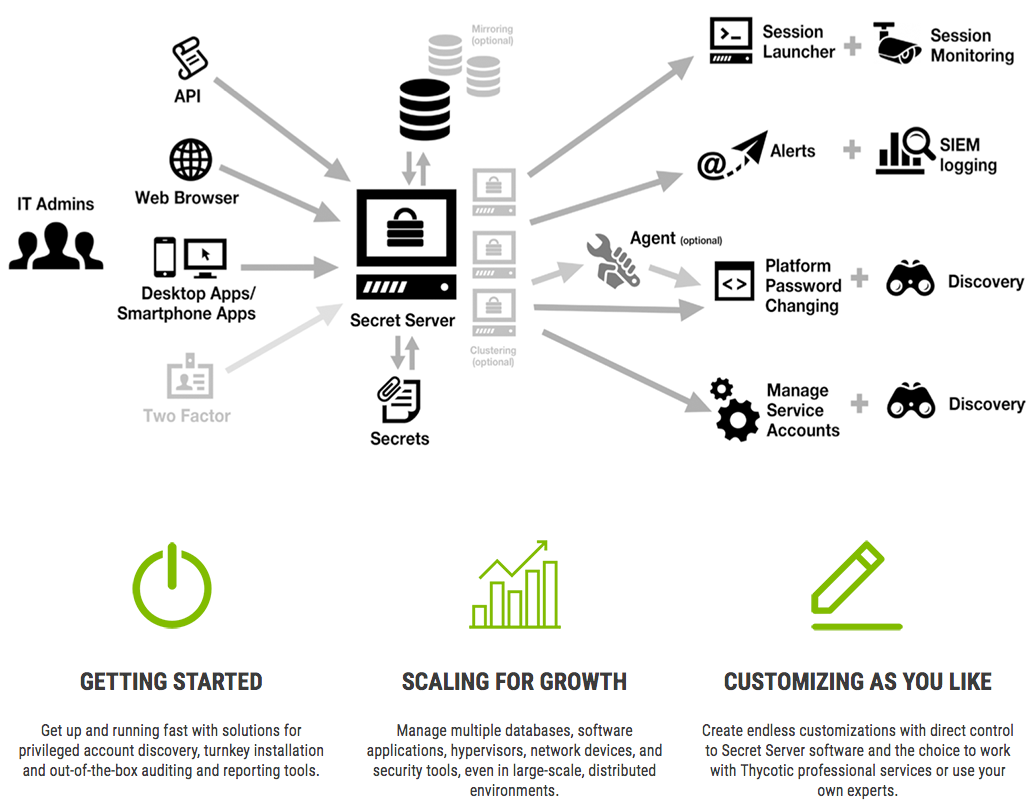
Thycotic Secret Server is a comprehensive solution designed to enhance enterprise security by safeguarding sensitive data, such as passwords, credentials, and other confidential information. It plays a vital role in protecting critical assets and preventing unauthorized access to valuable resources within an organization.
System Requirements for Setting Up Thycotic Secret Server
- Hardware and Software Requirements: Thycotic Secret Server requires a server with adequate processing power, memory, and storage capacity to ensure optimal performance. It is compatible with various operating systems and databases, with specific versions detailed in the official documentation.
- Recommended Configurations: To achieve the best results, it is recommended to deploy Thycotic Secret Server on a dedicated server with sufficient resources. Additionally, configuring network settings, firewall rules, and security protocols can help in maximizing the system's efficiency.
Installation Process of Thycotic Secret Server
- Step-by-step Installation: The installation of Thycotic Secret Server involves downloading the software, running the setup wizard, configuring database settings, defining administrative credentials, and finalizing the installation process. Detailed instructions can be found in the installation guide provided by Thycotic.
- Server Configuration Guidelines: During installation, it is crucial to set up server settings, including SSL certificates, backup options, and email notifications. These configurations ensure the security and functionality of Thycotic Secret Server.
Configuring Security Policies in Thycotic Secret Server
- Access Controls and Permissions: Thycotic Secret Server allows administrators to create granular access controls and assign specific permissions to users based on their roles and responsibilities. This helps in restricting unauthorized access to sensitive information.
- Security Policy Management: Administrators can define security policies within Thycotic Secret Server to enforce password complexity requirements, expiration intervals, and other security measures. Regularly reviewing and updating these policies is essential for maintaining a secure environment.
Integrating Thycotic Secret Server with Active Directory
- Benefits of Integration: Integrating Thycotic Secret Server with Active Directory streamlines user authentication processes, centralizes user management, and enhances security by leveraging existing directory services. This integration simplifies user access and ensures consistency across the organization.
- Configuration Guidelines: To integrate Thycotic Secret Server with Active Directory, administrators need to configure LDAP settings, map user attributes, and establish synchronization schedules. Following the integration best practices can optimize system performance and user experience.
Backup and Recovery Strategies for Thycotic Secret Server
- Importance of Backups: Regular backups are essential for protecting data stored in Thycotic Secret Server against loss, corruption, or unauthorized modifications. Implementing automated backup routines and off-site storage solutions can help in ensuring data availability in case of emergencies.
- Best Practices for Recovery: Establishing robust backup and recovery strategies involves creating backup schedules, testing restoration procedures, and monitoring backup integrity. Adhering to best practices can minimize downtime and mitigate data-related risks effectively.
Monitoring and Auditing in Thycotic Secret Server
- Monitoring Capabilities: Thycotic Secret Server offers comprehensive monitoring features that enable administrators to track user activities, access attempts, and system events in real-time. Monitoring logs and generating reports can help in identifying security incidents and ensuring compliance with regulatory requirements.
- Auditing for Compliance: The auditing functionalities of Thycotic Secret Server assist organizations in maintaining compliance with security standards, such as PCI DSS, HIPAA, and GDPR. Regular auditing and reviewing of security logs are essential for demonstrating adherence to industry regulations.
Scaling Thycotic Secret Server for Enterprise Environments
- Scaling Strategies: As the usage of Thycotic Secret Server grows within an enterprise, implementing scaling strategies becomes crucial to accommodate increased data volumes and user demands. Strategies may include deploying additional servers, optimizing database configurations, and load balancing techniques.
- Performance Optimization: To optimize the performance of Thycotic Secret Server in enterprise environments, administrators can fine-tune system settings, allocate resources efficiently, and implement caching mechanisms. Regular performance monitoring and tuning can sustain the system's effectiveness as it scales.
Final Summary

As we conclude our journey through setting up Thycotic Secret Server for enterprise security, remember that a robust security framework is essential in today's digital landscape. Stay vigilant, stay secure.