As Thycotic Secret Server vs CyberArk: Which One is Better? takes center stage, this opening passage beckons readers with casual formal language style into a world crafted with good knowledge, ensuring a reading experience that is both absorbing and distinctly original.
In this comparison, we delve into the key features, security offerings, scalability options, and user experience of Thycotic Secret Server and CyberArk to determine which one comes out on top.
Thycotic Secret Server vs CyberArk

Thycotic Secret Server and CyberArk are two leading solutions in the privileged access management (PAM) space, offering robust features to secure sensitive data and manage privileged accounts. Let's compare the key features of these platforms and delve into their security offerings, scalability options, and user experience.
Key Features
- Thycotic Secret Server: Provides secure storage and management of privileged account credentials, session monitoring, password rotation, and integration with third-party tools.
- CyberArk: Offers comprehensive privileged access management solutions, including password vaulting, session isolation, threat analytics, and privilege escalation detection.
Security Offerings of Thycotic Secret Server
Thycotic Secret Server focuses on protecting sensitive data by securely storing and managing privileged account credentials. It offers features like password rotation, session monitoring, and integration with other security tools to enhance overall data protection.
Scalability Options in CyberArk
CyberArk provides scalable solutions to meet the growing needs of organizations. It offers flexible deployment options, such as on-premises, cloud, or hybrid models, allowing businesses to scale their privileged access management infrastructure as required.
User Interface and User Experience
- Thycotic Secret Server: Known for its user-friendly interface, making it easy for users to navigate and manage privileged accounts efficiently.
- CyberArk: Offers a comprehensive yet complex user interface that may require training for optimal use, but provides advanced features and customization options.
Implementation and Integration
When it comes to implementation and integration, Thycotic Secret Server and CyberArk offer distinct features and capabilities that cater to different needs and preferences.Thycotic Secret Server:
Ease of Implementation
Thycotic Secret Server is known for its user-friendly interface and straightforward implementation process. The platform provides step-by-step guidance and documentation to help users set up and configure the solution efficiently. Additionally, Thycotic offers excellent customer support to assist with any implementation challenges that may arise.
Use Cases where Thycotic Secret Server Excels in Implementation
- Small to medium-sized businesses looking for a quick and easy way to secure their privileged account credentials.
- Organizations with limited IT resources seeking a simple yet effective solution for managing and protecting sensitive information.
- Companies that prioritize user-friendly interfaces and seamless integration with existing systems.
CyberArk:
Integration Capabilities with Other Security Tools
CyberArk is recognized for its robust integration capabilities with a wide range of security tools and technologies. The platform seamlessly integrates with various third-party applications, allowing organizations to create a comprehensive security ecosystem tailored to their specific needs. CyberArk's integration options enable users to leverage the full potential of their existing security infrastructure.
Comparison of Integration Process
- Thycotic Secret Server offers a more straightforward integration process compared to CyberArk, making it an ideal choice for organizations looking for quick and hassle-free implementation.
- CyberArk's extensive integration capabilities make it a preferred option for enterprises that require a highly customizable and interconnected security environment with multiple tools and systems.
In conclusion, both Thycotic Secret Server and CyberArk excel in implementation and integration, each offering unique strengths to meet the diverse requirements of organizations in safeguarding their sensitive data and privileged accounts.
Security Capabilities
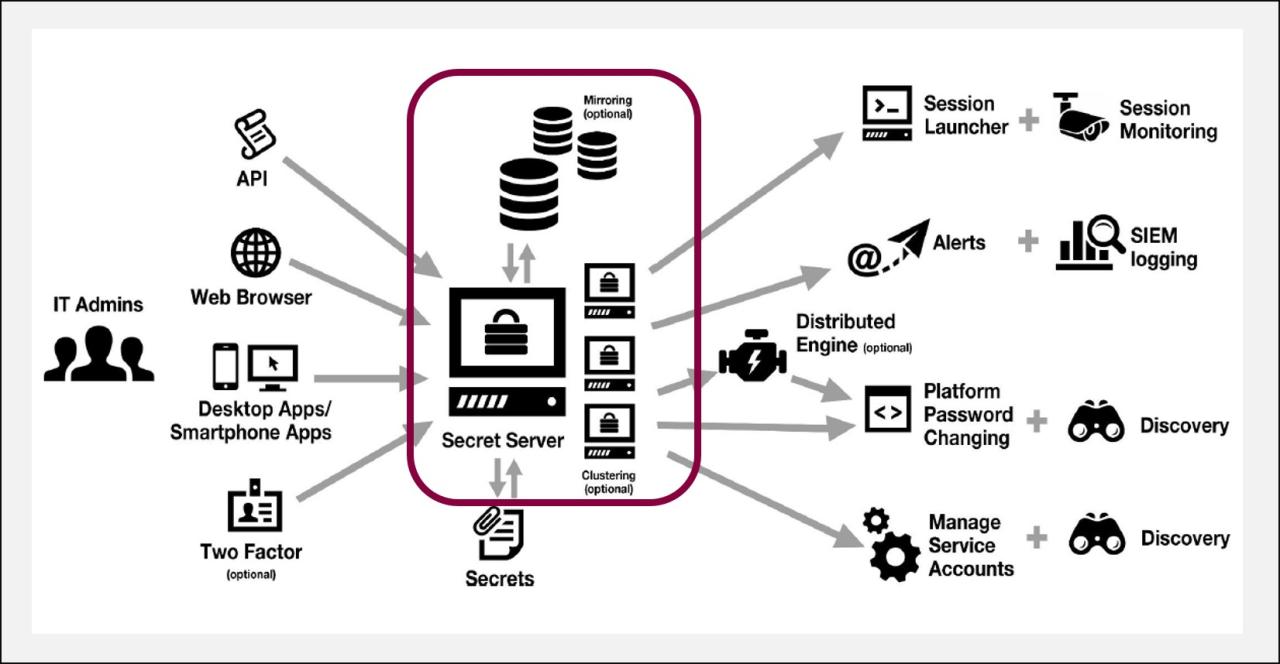
Thycotic Secret Server and CyberArk are both renowned for their robust security capabilities, offering various features to protect sensitive data and manage privileged access effectively.
Thycotic Secret Server Privileged Access Management
Thycotic Secret Server provides a comprehensive privileged access management solution, allowing organizations to secure, manage, and monitor privileged accounts and credentials. It offers features such as password rotation, session recording, and multi-factor authentication to enhance security.
CyberArk Threat Detection and Response
CyberArk excels in threat detection and response mechanisms, utilizing AI-driven analytics and real-time monitoring to identify suspicious activities and potential threats. It offers privileged threat analytics to detect and respond to threats promptly.
Encryption Methods
Both Thycotic Secret Server and CyberArk employ strong encryption methods to safeguard sensitive data. They use industry-standard encryption algorithms such as AES (Advanced Encryption Standard) to ensure data confidentiality and integrity.
Password Management Security
Thycotic Secret Server and CyberArk prioritize secure password management practices. They enforce password policies, implement secure password storage mechanisms, and offer privileged session management to prevent unauthorized access and protect against credential theft.
Support and Maintenance
Support and maintenance are crucial aspects to consider when choosing between Thycotic Secret Server and CyberArk. Let's delve into the available options and quality of customer service for each platform.
Thycotic Secret Server Support Options
Thycotic Secret Server offers various support options for its users, including phone support, email support, live chat, and a knowledge base. Users can easily access resources and get assistance when needed. The support team is known for being responsive and helpful in resolving issues promptly.
CyberArk Maintenance Requirements
In enterprise environments, CyberArk requires regular maintenance to ensure optimal performance and security. This includes applying patches, updates, and configurations as needed. CyberArk also provides documentation and guidelines for maintenance tasks to help users manage the platform effectively.
Customer Service Quality Comparison
When it comes to customer service quality, Thycotic and CyberArk both have dedicated support teams to assist users. However, Thycotic is often praised for its personalized and attentive customer service, with users reporting positive experiences with their support interactions. On the other hand, CyberArk's customer service is also reliable but may not always offer the same level of personalized assistance as Thycotic.
Community Forums and Resources
Both Thycotic Secret Server and CyberArk have active community forums and resources available for troubleshooting and sharing best practices. These forums serve as valuable platforms for users to seek help from peers, share tips, and stay updated on the latest developments in the cybersecurity landscape.
Users can benefit from the collective knowledge and experiences shared within these communities to enhance their usage of the platforms.
Final Review
In conclusion, after exploring the various aspects of Thycotic Secret Server and CyberArk, it's evident that each platform has its strengths and weaknesses. Ultimately, the choice between the two depends on specific needs and preferences.